Social engineering, I talk about this a lot, but it's worth the reiteration. Hacking into a network isn't an easy task, it takes training, experience, and finesse to silently retrieve the desired data and depart without leaving any signs behind. Why even attempt an attack when the user can do the work for them?
All it takes is a single click to open an email and BOOM! Your entire network is locked and encrypted... "Whoops...all I did was open an email." To help everyone better understand this method of social engineering, I will break it down into steps.
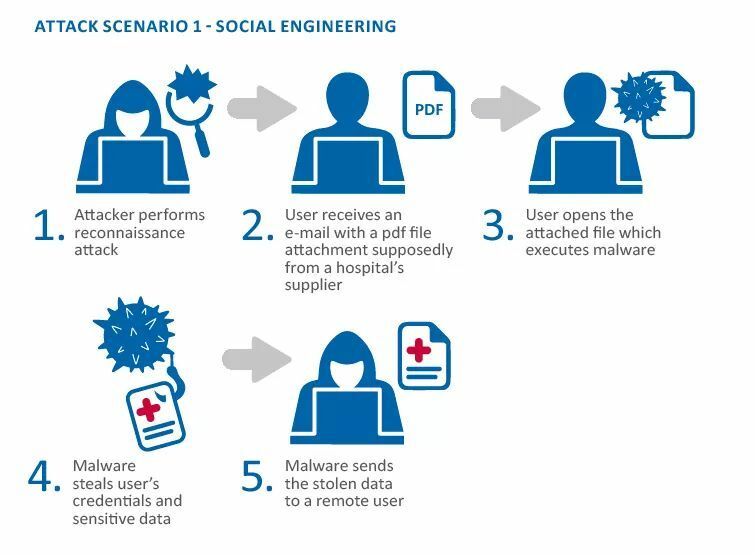
The first process an attacker wants to do is find his target. This could be a small business, major corporation, government, or even just a residential network.
Once the attacker chooses his victim an email is sent to the most vulnerable user. This user receives an email with an attachment, the most common type is with a PDF file. There are hundreds of other forms of social engineering, but we're only talking about emails and attachments today.
If the attacker's research was correct then the user will ultimately click on the email and open the attachment. The instant this happens, malware hidden within the file is executed and begins stealing and encrypting data. This is the point of no return, the user has lost. The attacker has access to the network, attached computers, servers, phones connected to the internet, everything.
Does the user have a contingency plan for this? If not, they have lost all of their data, there is nearly 0% chance of recovering encrypted files. No matter what a ransomware alert says, never pay the ransom; this is just another way for the attacker to get money from you. You will not get your files decrypted and you will be out more money.
So what do we say to social engineering? "Not Today!"
The first step in avoiding social engineering is to never open an email that looks suspicious. If an email looks odd, contact your security or IT department and have them look at it. NEVER forward a suspicious email! The possibility of the recipient accidentally opening the email, especially when it is shown from a user in their own network is too great.
If you do not have anyone to inspect the email, check the sender's address and the email source code (If you are proficient enough to do so). If you are uncertain, just stay on the safe side and delete the email. If you're expecting an email and this email looks suspicious, call the sender and confirm if that is the email they sent. It is worth the extra 5 minutes to check rather than losing thousands of dollars, data, and potential law suits.
Stay alert and aware when reading emails! The human element is the weakest link in any technology. Don't be that weak link!