This comprehensive article documented the Australian Department of Health (DoH) COVIDSafe contact tracing App, How it holds personal data of the Australian and Immigrant, data stored on the cloud and it covers the threats and risks to the security, location, and privacy of its Australian citizen.
CovidSafe App-Australia2019.
1. Introduction:
★The Commonwealth of Australia consists of six states and two self-government territories granted under the Commonwealth federation. The Department of Health and the Australian Health Protection Principal Committee (AHPPC), sectors are solely responsible for taking primary public health measures to respond to COVID-19 pandemics, such as testing, contact tracing, development, social distancing, health standards, and requirements, travel and border restrictions, and implementing protocol control across Australian regions. DoH and AHPPC followed the country’s constitutional structure and relevant laws, plans, and arrangements to form a Covid Safe App and measures.
★The Department of Health (DoH) from the Australian Government has now decided that they want to develop a COVID-19 contact tracing app for Australian and non-immigrant citizens. The app data will be hosted on a major U.S based public cloud provider to host users COVID-19 CovidSafe data. DoH can gain a better view of the health status of what each citizen holds, and wants to link that data to other data that they hold about each citizen through the virtual identical workflow for contact tracing app.
★It helps DoH health officials, researchers, and other public agencies to govern the citizens through the cloud system in an effective manner. DoH approached a major U.S based cloud service provider (CSP) to host the data on the cloud and DoH pressed the Government to host the data within the Australian territory to assure the privacy data security, data protection, and data sovereignty for users and its citizens.
1.1 Scope of the COVIDSafe app Analysis:
(I) This section summarizes the list of requirements for the DoH COVID-19 CovidSafe App cloud project, based on the discussion in the following sections.
(II) Existing threats and risks to the security of user data- CovidSafe App.
(iii) To analyze the possible threats to the privacy of a user’s data, location, and activities from the use of the CovidSafe app.
(iv) To analyze the existing and ongoing issues of data sovereignty that may apply to the storage of CovidSafe App data in U.S. based Cloud storage within Australia territory.
(v) Types of Security controls and measures to take.
Security controls:
Possible security controls that would prevent the loss or breach of user data
2. Privacy controls:
To analyze user privacy, data privacy, location, and activity of the user.
3. Data sovereignty controls:
To ensure that the CovidSafe App data remains under Australian data sovereignty laws.
1.2 Background Issues:
★The sudden increase in COVID-19 pandemic cases worldwide has caused considerable disruption in 215 countries and territories around the world. However, a number of countries have started to use an individual tracking approach to try and contain the spread of the virus. A number of countries have developed mobile phone apps that track people and their movements. DoH to adopt the cloud-based solutions to support and centralize CovidSafe App information sharing across the DoH organization in a scalable, secure, and most cost-effective way.
Source: Google Search
1.3 Scope of the Risk assessment:
★This article presents a detailed assessment to support the Department of Health (DoH) with the CovidSafe App strategy and on-boarding process. This report documented the Department of Health (DoH) COVID-19 contact tracing App, holds personal data of the Australian citizens stored on the cloud and it covers about the threats and risks to the security, location, and privacy of its own citizen. DoH considers the project potentials, threats, and risks to the privacy and data management of App users, and propose multiple security, privacy, and Data sovereignty controls to strengthen the CovidSafe App on user mobile and the data on the DoH public cloud.
2. The CovidSafe App:
★The Australian Government Department of Health (DoH) developed an app called “COVIDSafe” in response to the COVID-19 pandemic emergency across Australia. COVIDSafe app helps to keep the community and the public workforce safe from coronavirus infections.
2.1 COVIDSafe App Technical Objectives:
★The CovidSafe app operates in the background on the user’s smartphone, it uses Inbuilt “Bluetooth technology” and looks for other CovidSafe app installed devices within the 10meter proximity, and records activities like Mobile number, Name, Postal code, Timestamp, Distance, Reference code, and duration of actual contact happened between the User-A and User-B. The App does not count or record or trace the location of the user. For instance, User-A and User-B stayed at the same location within 1.5 meters range about 15 minutes or lesser could be stored in the user’s App on the smartphone later data will be uploaded to the cloud system with the user consent upon agreeing when installing and signing up for the account. All of the stored data are encrypted with the highest encryption protocol and even the own-user could not decrypt either access it. The event information is stored in the App for the maximum period of “21 days” and when it surpasses the set time, data will be automatically deleted.
2.2 COVIDSafe App UI:
★The developed COVIDSafe App on Android and iOS platforms to assists DoH and health officials on contact tracing without compromising users’ personal privacy and data. The given below figures represent the user interface of the COVIDSafe app and what type of information is being asked while onboard, to understand what type of privacy, security, and data settings control invoked by the user on their mobile phones.

2. Personally identifiable information (PII)strategy for COVIDSafe app portal:
★The PII may range from common data elements such as names, addresses, dates of birth, and places of employment, to identity documents, Social Security numbers (SSNs) or other government-issued identifiers, precise location information, medical history, and biometrics.
★The given below walkthrough process helps to understand what and how the information from the users is gathered and organized, also provides an overview of the data collection, privacy, and technology used on the App.
✓Download and install the COVIDSafe app
✓Read about how we can stop the spread, then select “I want to help”
✓Read about how COVIDSafe works, then select “Next”
✓Read the information on registration and privacy then select “Continue”
✓Read the consent to your registration and contact information being collected, then select “I agree”
✓To register enter: Name, Age, Phone Number, Zip code, then select “Continue”
✓Enter your Phone number then select “Get PIN” to verify your number.
✓Enter the 6-digit PIN, then select “Verify”
✓Select “Proceed” Proceed to enable Bluetooth® and Notifications.
✓Once the user registered and given permission, a confirmation status indicates “COVIDSafe is active”.
3. Existing threats and risks to the security of user data:
★In COVIDSafe App efficiently create, collect, analyze, process the affected COVID-19 user data, store, maintain, disseminate, disclose, and dispose of unprecedented volumes of affected and non-affected users sensitive PII on the public cloud using cutting-edge technologies such as AI and Bigdata to centralize the data.
★The threats and risks elements of requested PII through the COVIDSafe App as shown in Figure.3.
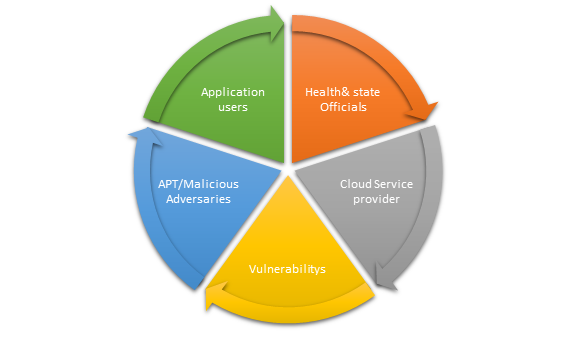
Figure.3 Threats and Risks of elements of user PII data.
3.1. Application users:
★Once the user successfully completed the onboard process and enabled Bluetooth function, they receive information about COVID-19 and health-related notification from time to time. however, due to the popularity of the Bluetooth supported apps may take advantage of using users’ activity and started to obtain more data without users’ prior concern or knowledge on the background and that leads to additional data and privacy concerns to the DoH and public.
★The initial version of the COVIDSafe 1.0.11 App stored all tracing data that includes additional (Device IDs, timestamp) into an SQLite DB in plain text format, and the App does not have a root detection logic process which leads to the potential Linkage Attacks on the user mobile. That being said, the later version resolved the security issues.
Anonymized data collection:
★The CovidSafe App collects few anonymized data about users’ phone model, app version, and other undisclosed data methods to help app development company to improve the App efficiency and improve better user experience.
3.2. Health and State officials:
★COVIDSafe App is using the centralized method similar to the technique implemented by the Singaporean government “TraceTogether app” source code. However, the data collected from the general user remains less vulnerable due to the tokens shared between users but the affected users upload data to the server (AWS public cloud) is at risk, affected user data is at exposure to the attack, service provider, and future usage target by the DoH. Only DoH can assess a user’s identity, temporary IDs, and changing contact logs over a period of 21 days. this raises a concern on user tracking and data gathering, poses a serious threat to the data infiltrate, exposure to the leak, or an attack.
3.3 Cloud Service provider and Multiple vendors:
★In this project, DoH and DTA depend on the external service provider for Public cloud access, Protocol, App development, and hosting the CovidSafe App data within Australian regions. The Australian government has chosen a major US-based AWS cloud service provider (CSP) for overall hosting such as prototype, app development, and operational support to the DoH.
★Other multiple third-party companies are involved in cybersecurity-related support service, gosource, and shine on app development, Delv landed two contracts for app development and launch with the Doh and DTA. ★The privacy and security threats posed on data handling, app development, by different vendors are immense to the public and the government.
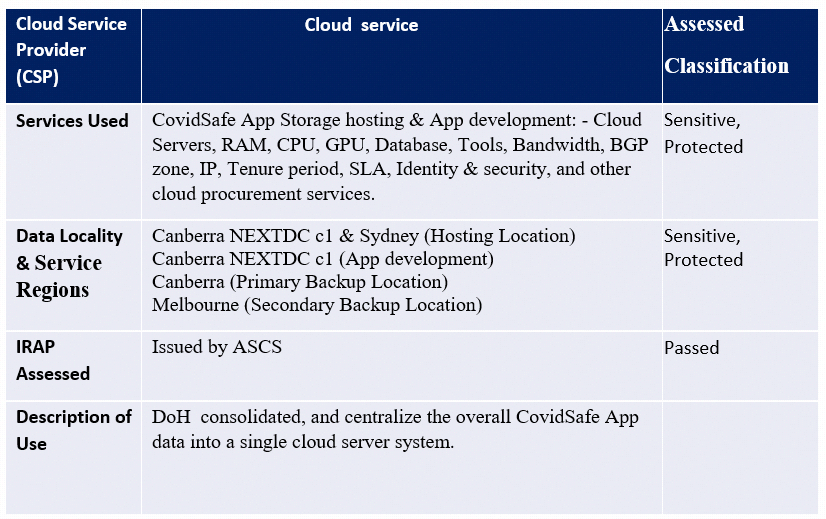
Table.1 Cloud service provider (CSP).
3.4 Vulnerabilitys:
★CovidSafe App Data from the user is stored on a user’s device and transmitted over the internet with the help of standard encryption to the hosted cloud server. Hence, the data is encrypted and safe. Although, still through some of the available loop-holes an attacker could possibly intercept such communications over the medium.
★ In the initial period of the launch, two major privacy and security concerns were in the protocol implementation that could potentially allow malicious third parties to ascertain static identifiers for users. During the handshake between the users, the same TempID would be returned back to the devices, pose a threat to the TempID patterns. Few more issues were left unresolved when running in GATT mode the payload, and device identifier without redesigning the protocol.
3.5 APT/Malicious Adversaries:
★Around the globe, many public sectors released algorithms and source code of their contact tracing apps, potential adversaries take advantage of the open-source materials and learned architecture to manipulate the system through various attack methods. In urban areas, attackers could use a Bluetooth broadcaster or receiver to conduct a safe attack without leaving footprints. on other hand, falsified or fake apps are available over the play store or iOs, thousand of people could be the data victim if DoH doesn’t make propaganda to the Australian citizens.
3.6 Data at Rest:
★The data present at the hosted AWS servers are exposed to the potential risk to the APT hackers. It is essential, and a big concern that hosted servers and CSP infrastructure have defense-in-depth security layers over storage and IAM. The major concern is over the applications and software used by authorized DoH officials on their systems, any outdated OS, software, plugins, tools, browsers, could trigger a path to the attacker and gain access to the hosted servers through a proper channel.
★The transmitted data to the server location is unknown also If the App’s data encryption is compromised it could be intercepted and data theft will occur.
3.7 Bluetooth Security and Issues:
★In fact, CovidSafe App implemented many security modules to protect the data and privacy of the users.
★Enabling Bluetooth 24/7 is at a security risk.
★The end-user device is visible to the attacker within 100m proximity, which helps to mask hacker identity.
★A Simple hacking technique could gain access to mobile internal data.
★Forced-pairing could be done easily.
★other 3rd party apps take advantage of the user data for various purposes.
4. The Privacy Security and Location of the App data:
★In this section, the following risk factors were taken into considerations to facilitate privacy security, and location risks and concerns to the CovidSafe App. The privacy and risk factors are constructed into a more detailed perspective in this assessment report along with the guidance and control recommendations on privacy and security.
4.1 PII Levels of Trust:
★DoH and the Australian legalization bureau distinguished the information into two groups, an individual identity, and group identity according to The Health Privacy Principles (HPPs) in the Health Records and Information Privacy Act 2002 (HRIP Act), and The Australian Privacy Principles (APPs) in the Commonwealth Privacy Act and The Privacy Amendment (Public Health Contact Information) Bill 2020 falls under the Biosecurity Act 2015 as of 25th-Apr-2020.
★PII from these two categories is traceable and can be linked to identify an individual only by the DoH health officials, clearly stated to the public and lawmakers not assessed neither controlled by the law enforcement agencies. Thus, DoH management needs to assign a person to conduct a privacy risk model on data management and control to refine levels of trust.
4.2 PII Privacy boundary lines:
★DoH not yet defined the privacy boundary lines on employees’ sensitive PII data, and the DoH directorate should aware the other Australian agency might access the data of any individuals. Despite the fact of the new law under the Privacy Act (1988) BILL and senate committee addressed to the general public, access prohibited to Australian law enforcement on CovidSafe App data even under the court order in any jurisdictions. But new legislation may override other Commonwealth and state and territory laws after the end of the pandemic.
4.3. Data Process (Collecting, Storing, Handling):
★The data process actions performed on cloud systems operations include creation, collection, retention, SIEM, analysis, data-in-transit, data backup and disclosure, and disposal of PII from the cloud. Thus, data actions indicate data handled by individuals are problematic threats, and DAS required to conduct a risk assessment on data handling and management.
4.4 CovidSafe Source code concerns:
★However, the CovidSafe App source code was published by Digital Transformation Agency (DTA) to the public and researchers to scrutinize the technical bugs. but the government did not release the source code for the server. It left researchers puzzled to further scrutiny how the data is store under which encryption criteria. On the contra, the Singapore government is very liberal on publishing both the source code of the app and the server-side.
4.5 Location Tracking-CovidSafe App:
★The data retention and location tracking identified several factors of Information and Communications Technology (ICT) that could trigger privacy and security concerns over the App data at rest and in-transit. There is an exception, the NHS Act, permits DoH to share or exchange health surveillance information activities between interstates and the World Health Organization (WHO).
★The Australian Telecommunications Act (1997) enforced PII related information and disclosure by the Tier 1,2,3 providers on their infrastructure and public services, that includes (phone, internet services, license, location) on using mobile phones. The Privacy Act (1988) permits the disclosure of information to law enforcement with a court order and the required reasons meet the matter of national security to charge a suspect or criminal. The data uploaded to the server falls under the above-mentioned Act and perplexing to the legislation.
★ASIO Act 1979, and Crime Act (1914), allow the room for use of surveillance and tracking. The mass surveillance legislation in these states prohibits tracking through GPS without the explicit consent of an individual on CovidSafe data. In section 5 data sovereignty extensively covered the federal laws and regulations on data retention, collection, and location of an individual citizen in detail.
4.6Automated Data Deletion:
★The data stored on the user's mobile phones, after 21 days will be automatically deleted based on a rotation scheme and the deleted can be recovered using the recovery software. If any user-submitted the data to the server, these data won’t be destroyed until the end of the COVID-19 Pandemic, this option poses a threat to the user who wanted their data to be deleted.
4.7 CovidSafe data period:
★One of the major agitations from the general public is about how long to keep up with the App, and what’s the status of the stored data. The Minister for Health (MoH) to predict and determine the end of the App data period. When the MoH and DoH release an official statement, the use of the CovidSafe App is no longer required or mandatory by the general public in Australia. After the prolonged period, the App must not be available for download from any sources, no further data collected from the App, no more data access to any officials, restrict admin access to App data and take precautionary measures to wipe the data permanently from the server, destroy the server, cancel the contract from the provisioned date from the government.
4.8 security point of view:
★From a security point of view, the App posed a few technical vulnerabilities due to the design flaws, and generic nature of the Bluetooth relay attacks unavoidable in the present versions. The App does not appear to increase the attack surface for most of the users, and those using other Bluetooth Related Apps on their mobile phones should be cautious about data and security settings on the App.
5. Data sovereignty:
★The Australian state, federal and territory laws are likely divergent to the cloud and information act laws that allow the AWS cloud provider to guarantee that adequate security measures, compliance, risk assessment have done to protect the CovidSafe data.
5.1 Governance, Risk, and Compliance:
★To evaluate the potential risks inherited to the cloud environment from the CSP can be mitigated through the evaluation of Australian Privacy Principles.
5.1.1 Data Retention and Location Tracking-CovidSafe App:
★The Australian government introduced Privacy Act (1988) to regulate and control the public (services, government agencies) and private sectors handling the PII and other sensitive information of individuals within its jurisdictions and also with the CSP.
★The data retention and location tracking identified several factors of Information and Communications Technology (ICT) that could trigger privacy and security concerns over the App data at rest and in-transit within Australian soil.
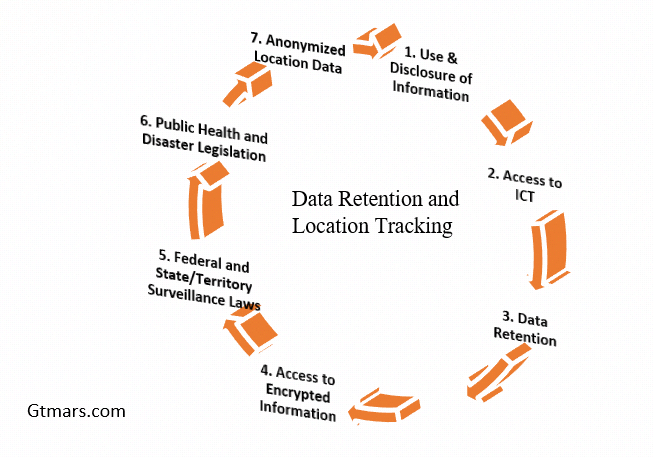
Figure.4 Data Retention and Location Tracking-CovidSafe App.
5.1.2 Use and Disclosure of Information:
★The Australian Telecommunications Act (1997) enforced PII related information and disclosure by the Tier 1,2,3 providers on their infrastructure and public services, that includes (phone, internet services, license, location) on using mobile phones. The Privacy Act (1988) permits the disclosure of information to law enforcement with a court order and the required reasons meet the matter of national security to charge a suspect or criminal. The data uploaded to the server falls under the above-mentioned Act and perplexing to the legislation.
5.1.3. Access to ICT for Law Enforcement:
★The Australian Telecommunications (Interception and Access) TIA Act 1979 provisioned rules, policies, and procedures that are applicable Australian Security Intelligence Organization (ASIO) to lawfully intercept or access the ICT-related data if a person is injured or in the state of dying for a matter of national security. for instance, if a person could possibly infected or passed away due to the COVID-19 virus, the App data can be accessed through this law and collide with the new BILL.
5.1.4. Data Retention Technical objectives:
★The TIA Act law applies data retention maneuver, telecom companies are subjected to retain a given set of telecom data such as the location of the device, connection data, and not the actual user content to be kept for the minimum period of two years, also to ensure the CIA triad principles, such information should be protected by encryption technology.
5.1.5. Access to Encrypted Information:
★In 2018, the Australian government passed the Telecommunications and Other Legislation Amendment (Assistance and Access) Act 2018 to enhance and elaborate the access powers on the ICT to improve the ability of the encryption and decryption of data. That implies the App data can be an oversight by them.
5.1.6. Federal and State/Territory Surveillance Laws:
★ASIO Act 1979, and Crime Act (1914), allow the room for use of surveillance and tracking. The mass surveillance legislation in these states prohibits tracking through GPS without the explicit consent of an individual on CovidSafe data.
5.1.7. Public Health and Disaster Legislation:
★The National Health Security Act 2007, Biosecurity Act 2015, disaster or emergency laws, and other state public health laws do not contain any enforcement on monitoring mobile phone traffic and location data on responding to the ongoing pandemic. There is an exception, the NHS Act, permits DoH to share or exchange health surveillance information activities between interstates and the World Health Organization (WHO).
5.1.8. Anonymized Location Data:
★In April 2020, one of the major ISP (Vodafone Australia) had provided mobile phone-based location data to the federal and NSW government to monitor citizen activities on social distancing during the pandemic.
5.2 Automated Data Deletion:
★The data stored on the user's mobile phones, after 21 days will be automatically deleted based on a rotation scheme and the deleted can be recovered using the recovery software. If any user-submitted the data to the server, these data won’t be destroyed until the end of the COVID-19 Pandemic, this option poses a threat to the user who wanted their data to be deleted.
5.3 CovidSafe data period:
★One of the major agitations from the general public is about how long to keep up with the App, and what’s the status of the stored data. The Minister for Health (MoH) to predict and determine the end of the App data period. When the MoH and DoH release an official statement, the use of the CovidSafe App is no longer required or mandatory by the general public in Australia. After the prolonged period, the App must not be available for download from any sources, no further data collected from the App, no more data access to any officials, restrict admin access to App data and take precautionary measures to wipe the data permanently from the server, destroy the server, cancel the contract from the provisioned date from the government.
6. Recommended Security controls:
✓Encryption- Apply AES 256 bit.
✓Database- maintained and updated regularly with standard encryption principles.
✓Data breach- DHHS notify it to the OAIC and to the affected individuals. DTA has a similar protocol and it should be integrated into a centralized notification protocol.
✓Security breach- At present, the Office of the Victorian Information Commissioner (OVIC) handles the security breach. It is not synchronized with other Australian Cyber Security Centre (ACSC) and CERT.
✓Data Security standards- DoH should Inherit Victorian Protective Data Security Standards V2.0.
✓Inquiries or complaints- Data collected by the app should be added encrypted and stored.
✓PII- Secure Data Deletion of PII.
✓IAM- To Monitor and manage access privileges.
✓Physical Security- Monitor, Track, Train, add 6 layers of DC security, and control.
✓Data control, Data Replica, Multi-tenancy.
7. Recommended Privacy controls:
DTA acted on behalf of the Australian government and it will provide the infrastructure and operational support services for the National COVIDSafe Data Store where the data resides and available as a service to the DoH department. DTA should further enact more formalized frameworks into its decision body to safeguard the privacy and security of the citizens.
✓ Client Device/Application Protection.
✓ Publish the source code on the server-side.
✓To prevent unauthorized third-party access.
✓The data sensitivity level should be documented.
✓Content and access permissions should be implemented.
✓Reassess Levels of Risk.
✓To conduct Governance (CCSL, PSPF, Privacy Act 1988), and training.
✓To monitor and manage access privileges.
✓Implement centralized (unified) breach notifications policy.
✓Internal procedures and practice of the cloud systems.
✓ Interstate- Citizens at the interstate border data are exchanged with different health bodies.
✓ Risk management- To assess and mitigate any risks to the App data.
✓ Data Privacy, security, and location implications on PII should be reassessed.
✓ Cloud-based messaging system- To anonymous user location with message masking features.
8. Recommended Data sovereignty controls:
The DoH and Federal government should adhere to the existing legislation on ICT and health sector Acts to intact the required new amendments to adopt the pandemic situation into its legislation by forming a legal and ethical framework guide to protect the privacy, data, security, and sovereignty of the Australian citizens.
✓TDIF accreditation — privacy, data protection, security, fraud control, risk management, and much more.
✓Cloud Platform annual audits.
✓Compliance Requirements:
ISAE 3402- International Standard on Assurance Engagements 3402 (SOC 1, SOC 2, SOC 3)
ISO/IEC 27001- Information security
ISO 27017- The international standard of practice for information security
ISO 27018 -Cloud Privacy.
✓ Biosecurity Determination 2020 and Biosecurity Act 2015 required reassessment on the changes.
✓ Bill does not impose mandatory action on installing App, but private entities mandate it. It should be addressed.
✓Privacy Amendment (Public Health Contact Information) Bill 2020- To integrate it with the existing federal Act listed in section 5.1.
Note: This Article documented the Australian Department of Health (DoH) COVID-19 contact tracing App, How it holds personal data of the Australian and Immigrant, data stored on the cloud and it covers the threats and risks to the security, location, and privacy of its Australian citizen.
It's an independent review and research study about the COVID-19 contact tracing App around the globe, Australian Department of Health (DoH) does not sponsor nor support this article.
If you have any queries related to the report, wanna learn more about it. Please, let me know about that in the comment section.
— — — — — — — — — THE END — — — — —— — — — ——
Quote of the day: You will never do anything in this world without courage. It is the greatest quality of the mind next to honor. — Aristotle
Explanation: A frog in a well never knows the vast ocean
Thanks for reading👍!
Only buy me a coffee if you enjoyed it 😊!!!
Appreciate it forever!!!
Have a pleasant day🌞!
— — — — — —— — ——— — — — — —— — — — —
About Me:
Founder of gtmars.com & plan2trip.com. From time to time I share knowledge in the digital world about Cybersecurity, Technology, the Space industry, Traveling, Japanese Haiku poems.
My blogs😂: Connect with the one you like!
https://hackernoon.com/u/gtmars.com
https://www.facebook.com/Gtmarscom-113569997170307

