Vulnerability management is the cyclical practice of identifying, classifying, remediating, and mitigating vulnerabilities.
★In computer security, a vulnerability is a weakness in the system, a threat actor can exploit the weakness, to perform unauthorized actions within organizational applications or network. To take advantage of a vulnerability, an attacker must have a minimum of one applicable tool or technique that will be wont to identify and connect with system vulnerability. During this frame, we also know vulnerability because of the attack surface. Vulnerability management is that the cyclical practice of identifying, classifying, remediating, and mitigating vulnerabilities. This practice refers to software vulnerabilities in computing systems.
★A security risk is usually incorrectly classified as a vulnerability. Using vulnerability with the identical meaning of risk can result in confusion. the danger is that the potential of a major impact resulting from the exploit of a vulnerability.
★A security risk is usually incorrectly classified as a vulnerability. Using vulnerability with the identical meaning of risk can cause confusion. The danger is that the potential of a major impact resulting from the exploit of a vulnerability. There are vulnerabilities without risk: when the affected asset has no value. We classify a vulnerability with one or more known instances of working and fully implemented attacks as an exploitable vulnerability — a vulnerability that an exploit exists.
(I)The window of vulnerability is that the time from when the protection hole was introduced or manifested in deployed software, to when access was removed, a security fix was available/deployed, or it disabled the attacker — see a zero-day attack.
(ii)A security bug (security defect) could be a narrower concept: there are vulnerabilities that aren’t associated with software: hardware, site, personnel vulnerabilities are samples of vulnerabilities that don’t seem to be software security bugs.
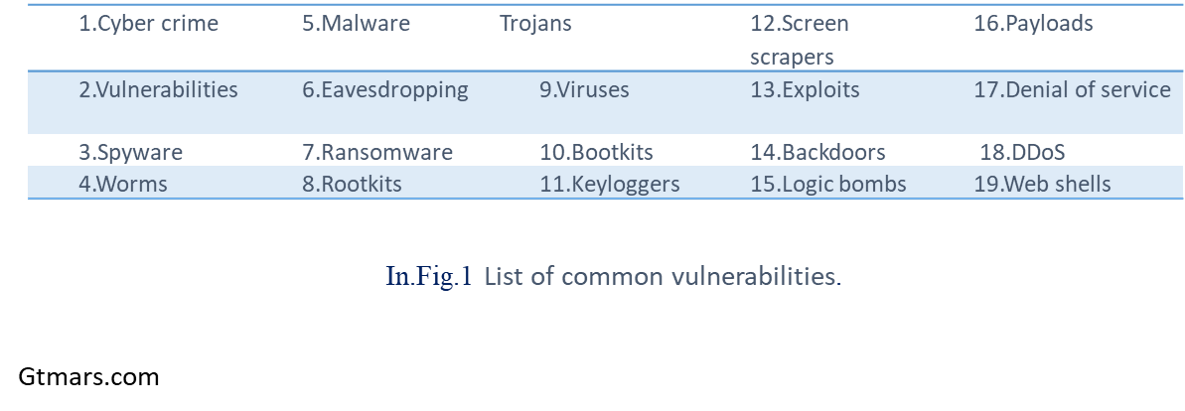
List of some common vulnerabilities:
Vulnerability management:
★it’s a “cyclical practice of identifying, classifying, prioritizing, remediating and mitigating” software vulnerabilities.
★Vulnerability management is an integral part of the computer and network security, and must not be confused with a Vulnerability assessment. We discover vulnerabilities with a vulnerability scanner, which analyzes a system in search of known vulnerabilities, like open/insecure ports, software miss configurations, and susceptibility to malware infections. Unknown vulnerabilities, like a zero-day attack, identified with fuzz testing, which might identify certain types of vulnerabilities, as a buffer overflow with relevant test cases. Test automation can facilitate such analysis.
★Antivirus software capable of performing heuristic analysis may discover undocumented malware if it finds software behaving suspiciously (such as attempting to overwrite a system file).
★This standardized service offers subsequent pre-vetted support services:
⍟Vulnerability scanning
⍟Web application assessment
⍟Phishing assessment
⍟Network mapping
⍟wireless assessment
⍟Database assessment
⍟Operating system security assessment (OSSA)
⍟Penetration testing
This process typically includes:
Discovering and cataloging all assets within your network.
Assigning a price to identified assets.
Identifying vulnerabilities and threats that exist for every asset.
Assessing the likelihood that they also exploit threats and
Building a recommendation for cost-effective mitigation. In the above section, potential impact, and also the likelihood of occurrence are projected, considerately of existing controls safeguards that would reduce the impact of the likelihood. Please, use the rating matrix to live the vulnerabilities, risk rating of Critical, High, Medium, low to explain the magnitude of risk.
Assessment types:
Assessment types Depending on the system a vulnerability assessment can have many sorts and levels.
1. Host Assessment, and
2. Network Assessment.
Host Assessment: A host assessment looks for system-level vulnerabilities like insecure file permissions, application-level bugs, backdoor, and computer virus installations. It requires specialized tools for the software and software packages getting used, besides administrative access to every system that ought to test. Host assessment is commonly very costly within the term of your time and thus barely used in the assessment of critical systems. Tools like COPS and Tiger are popular in host assessment.
Network Assessment: In-network assessment, one accesses the network for known vulnerabilities. It locates all systems on a network, determines what network services are in use, so analyzes those services for potential vulnerabilities. This process doesn’t require any configuration changes on the systems being assessed. Unlike host assessment, network assessment requires little computational cost and energy.
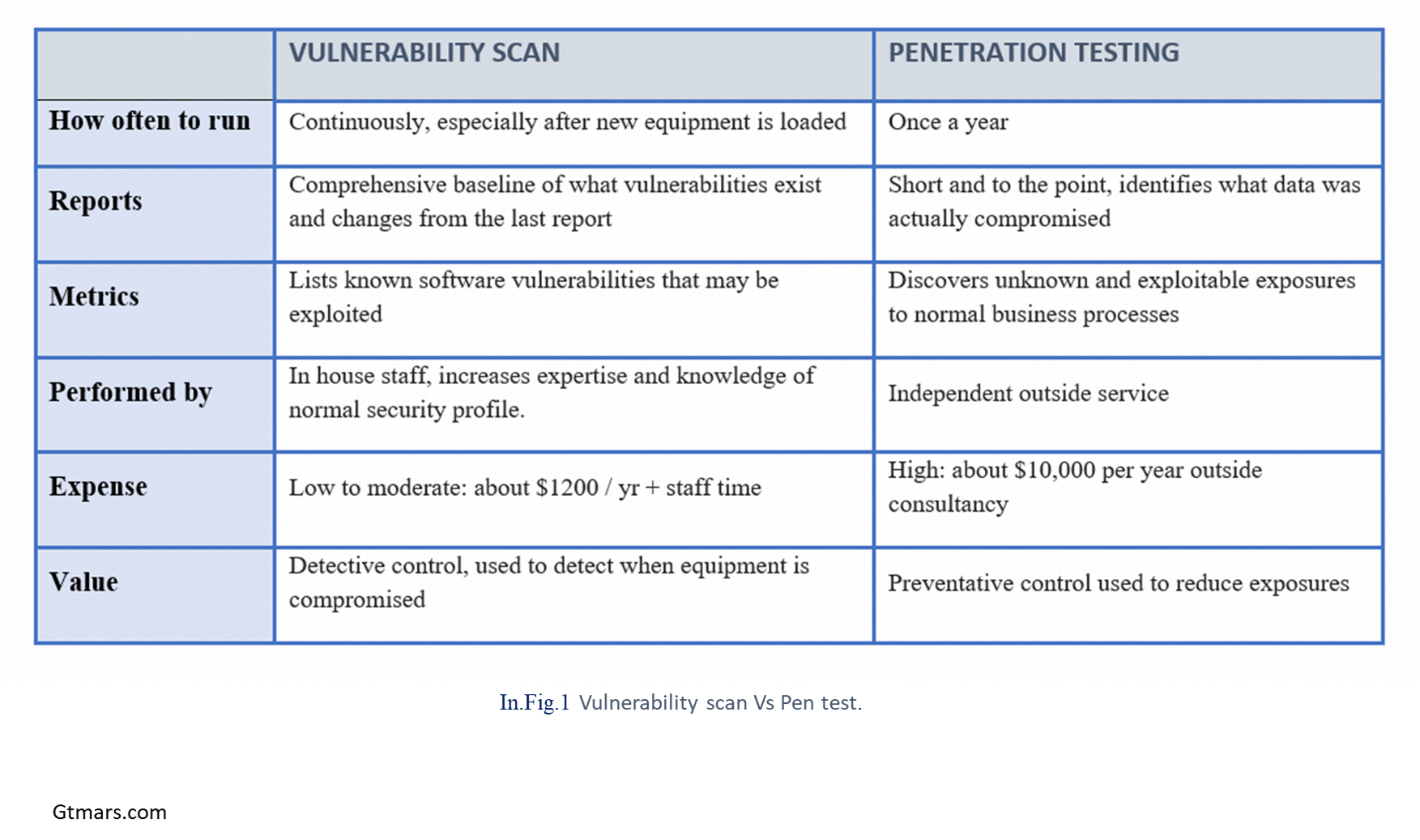
Vulnerability Assessment vs Penetration Testing
Vulnerability assessment and penetration testing are two unique testing methods. We differentiate them based on certain specific parameters.
Overall likelihood rating shows the probability that they may exercise a potential vulnerability within the construct of the associated threat environment, we must consider the following governing factors:
1. Threat-source motivation and capability
2. Nature of the vulnerability and
3. Existence and effectiveness of current controls.
Note: Please refer to the article “How to identify a Threat?, How to perform Risk Exposure Matrix and Threat Management,” for more information about the likelihood rating。
Impact Analysis:
The next major step in measuring risk level determines the adverse impact resulting from a successful threat exercise of a vulnerability.
★ System mission (e.g., the processes performed by the IT system)
★ System and data criticality (e.g., the system’s value or importance to an organization)
★ System and data sensitivity.
We can get this information from existing organizational documentation, such as the mission impact analysis report or asset criticality assessment report. A mission impact analysis (also known as business impact analysis (BIA) for some organizations) prioritizes the impact levels associated with the compromise of an organization’s information assets based on a qualitative or quantitative assessment of the sensitivity and criticality of those assets. An asset criticality assessment identifies and prioritizes the sensitive and critical organization information assets (e.g., hardware, software, systems, services, and related technology assets) that support the organization’s critical missions.
If this documentation does not exist or such assessments for the organization’s IT assets have not completed, the system and data sensitivity can be measured based on the level of protection required to maintain the system and data’s availability, integrity, and confidentiality (CIA) triad. Regardless of the method used to determine how sensitive an IT system and its data are, the system and information owners are the ones responsible for determining the impact level for their own system and information. In analyzing the impact, the approach is to interview the system and information owners. Therefore, the adverse impact of a security event can be described in terms of loss or degradation of any, or a combination of any, of the following three security goals: integrity, availability, and confidentiality. The following list provides a brief description of each security goal and the consequence (or impact) of its not being met:
1. Loss of Integrity.
2. Loss of Availability, and
3. Loss of Confidentiality.
Risk Determination:
We use a risk matrix during risk assessment to define the level of risk by considering the category of probability or likelihood against the category of consequence severity. This is a simple mechanism to increase the visibility of risks and assist management decision making. The determination of risk for a particular threat/vulnerability pair revealed as a function in the following aspects.
• The likelihood of threat sources attempting to exercise a vulnerability
• The magnitude of the impact should a threat-source successfully exercise the vulnerability
• The adequacy of planned or existing security controls for reducing or eliminating risk.
To measure risk, a risk scale and a risk-level matrix must establish.
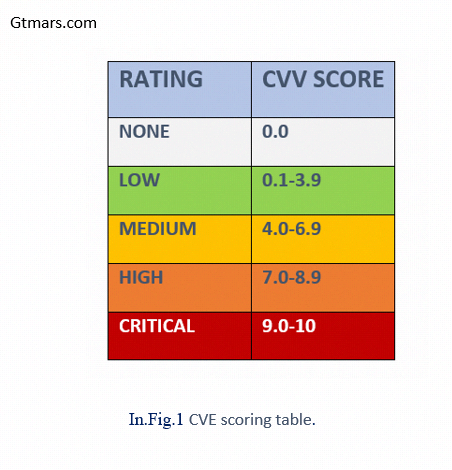
An Evolution of Scoring Security Vulnerabilities:
A simplified way to categorize security vulnerabilities called the Security Impact Rating (SIR). The following are the vulnerability SIR classifications.
Conclusion:
Vulnerability management is the cyclical practice of identifying, classifying, remediating, and mitigating vulnerabilities. we studied the simplified way to categorize security vulnerabilities using the standardized system.
— — — — — — — — — THE END — — — — —— — — —— —
Quote of the day: "He who steals a little steals with the same wish as he who steals much, but with less power." — Plato.
Thanks for reading👍!
Only Buy me a coffee if you enjoyed it 😊!!!
Appreciate it forever!!!
Have a pleasant day🌞!
— — — — — —— — — — — — — — — —— — — — —— —
About Me:
Founder of gtmars.com & plan2trip.com. From time to time I share knowledge in the digital world about Cybersecurity, Technology, the Space industry, Traveling, Japanese Haiku poems.
My blogs😂: Connect with the one you like!
https://hackernoon.com/u/gtmars.com
https://www.facebook.com/Gtmarscom-113569997170307
