This article describes the primary concepts associated with organizing and managing the system-related information security risk in organizations.
RISK MANAGEMENT OVERVIEW:
★This section describes the primary concepts associated with organizing and managing the system-related information security risk in organizations. To undertake the Managing information on security and the privacy-related task is complex, and it’s required a broad perspective which involves the entire organization from the Chief Technology Officer (CTO), Network Security Architect (NSA) providing the strategic vision and goals and objectives for the organization, to mid-level leaders planning, managing, and executing the visions, to associate level individuals developing, implementing, operating, and maintaining the organization’s strategic missions and business functions.
★Risk management is a reciprocal activity that includes mission and organization planning, network architecture, the SDLC processes, identify, evaluate, and prioritize risks followed by the application of resources to minimize, the control impact of unfortunate events or to maximize the realization of events.
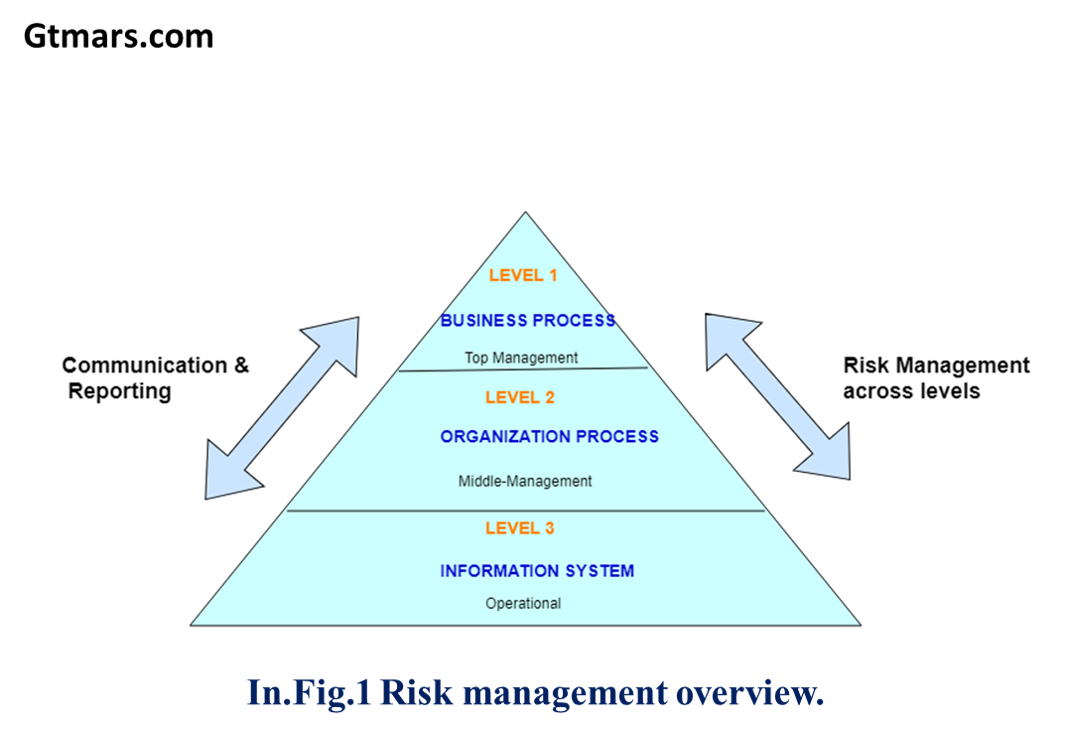
★The given below figure illustrates a multi-level approach to the organizational risk management flow. The communication between the business and organization is in bi-directional flow.
★The actions conducted at Level 1 and Level 2 are critical to preparing the organization to execute the risk management framework. Allocating roles and responsibilities for organizational risk management processes;

★If any organizations that fail to define and implement an effective network architecture approach will probably have difficulty in consolidating, optimizing, and standardizing their I.T infrastructures in a timely manner and also in-adequate preparation by organizations which leads to network redundancy as well as inefficient business concepts, costly and vulnerable systems, services, and customer applications. Importance of Risk management: The importance of risk management is to identify the potential problems before it emerges usually, they occur unconditionally. It helps the IT managers to balance the CAPEX/OPEX costs in the organization and also take protective measures and gains much control power. Risk management consists of three processes as Risk assessment, Risk Mitigation, and Risk evaluation. So, that risk-handling activities should be planned accordingly and invoked as needed across the software product life cycle to mitigate adverse impacts to achieve the desired goals. There are seven well-defined steps to carry out the successful execution in risk management.
The steps are;
✔Prepare: To execute a framework based on organization and a system-level perspective by establishing a context and priorities it.
✔ Categorize: system information is processed, stored, and transmitted. ✔Select: An initial set of controls required for the system to mitigate risk. ✔Implement: Implement the organizational controls within the system. ✔Assess: To determine if the controls are implemented correctly and operating as expected and producing the desired outcomes to meet the security and privacy standards.
✔Allow: To authorize individuals, other organizations are acceptable.
✔ Monitor: It helps to highlight whether defined strategies are effective in the system. Integration of Risk management into SDLC:
Integration of Risk management into SDLC:
★Minimizing a negative impact on an organization and the need for a sound basis in decision making is the fundamental reason organizations implement a risk management process for their IT systems. We must integrate effective risk management into the Software development life cycle (SDLC).
★The software development life cycle (SDLC) is a software framework defining tasks performed during each step in the SDLC process. It is a detailed structure followed by a software development team within the organization. It comprises a detailed plan describing how to develop, maintain, and replace specific software. There are five software developmental phases include Planning, Analysis, Design, Implementation, and Maintenance. However, the risk management method is the same regardless of the SDLC development phases. Risk management is an iterative process that can be performed during each major phase of the Software development life cycle.
SDLC PHASES:
1.REQUIREMENT ANALYSIS
2. DESIGN
3. IMPLEMENTATION (CODING)
4. TESTING
5.DEPLOYMENT & MAINTENANCE.
1.REQUIREMENT ANALYSIS:
SDLC CHARACTERISTICS: Project goals and high-level plans are to be determined from the endpoint. The following key will activities take place:
Identification of the development and business requirements.
2. Feasibility assessment.
3. Creation of project plan.
RISK MANAGEMENT PROCESS: To Identify risks are used to support the development of the system requirements.
2. DESIGN:
SDLC CHARACTERISTICS: This phase includes business rules, pseudo-code, layouts, and functional design documentation works. The following key activities will take place:
1. Design System model and
2. Design Infrastructure model.
RISK MANAGEMENT PROCESS: The risks identified in this phase later can support the security analysis, I.T architecture, and design tradeoffs in the system development
3. IMPLEMENTATION (CODING):
SDLC CHARACTERISTICS: Phase 1& 2, are formulated in order for an actual system. The following key activities will take place:
1. Development of Database and codes
2. Development of Infrastructure codes and
3. Documents divided into modules and units.
RISK MANAGEMENT PROCESS: This process supports the assessment of the system implementation against its requirements and within its modeled operational environment. Bugs must be logged and corrected.
4. TESTING:
SDLC CHARACTERISTICS: Codes are integrated and deployed in the testing environment. The following key activities will take place:
1.functional testing. 2.Unit testing, 3. Integration testing, 4. System testing and 5. Acceptance testing.
RISK MANAGEMENT PROCESS: whenever major changes are made to the system module in its operational, production environment (e.g., new system interfaces). re-authorization is performed for any major changes. It should guarantee the testing module is performed correctly and all the bugs have been rectified.
5. DEPLOYMENT & MAINTENANCE:
SDLC CHARACTERISTICS: After testing, the product is delivered to the customer.
RISK MANAGEMENT PROCESS: After the risk assessment, it is ready to be delivered to the customer.
SDLC CHARACTERISTICS: Product maintenance will take place.
RISK MANAGEMENT PROCESS: Post-delivery maintenance and product support will be provided as per the agreement.
Conclusion:
In this article, we discussed the primary concepts associated with organizing and managing the system-related information security risk in organizations.
— — — — — — — — — THE END — — — — —— — — —— —
Quote of the day: "Excess of grief for the dead is madness; for it is an injury to the living, and the dead know it not." — Xenophon.
Thanks for reading👍!
Only Buy me a coffee if you enjoyed it 😊!!!
Appreciate it forever!!!
Have a pleasant day🌞!
— — — — — —— — — — — — — — — —— — — — —— —
About Me:
Founder of gtmars.com & plan2trip.com. From time to time I share knowledge in the digital world about Cybersecurity, Technology, the Space industry, Traveling, Japanese Haiku poems.
My blogs😂: Connect with the one you like!
https://hackernoon.com/u/gtmars.com
https://www.facebook.com/Gtmarscom-113569997170307
