Thank you goes out to B4M, FL, and K. for helping with this month's Support. It helped me get more sdcards (I am waiting on now) which I needed for my next project. Big thank you. :)
Never receive anything you do not have permission to receive.
For ethical purposes. A demonstration script only meant to be used to check your own devices. Can be handy to filter your devices to detect which ones are disconnecting most often- devices disconnected frequently give away handshakes more often-- a major vulnerability that can be discovered using this is conrolled setting. Solution: move those devices closer to your router.
Also a good way to see what networks your devices appear to be searching for. All of this can lead to travel movements being mapped out, a privacy concern.
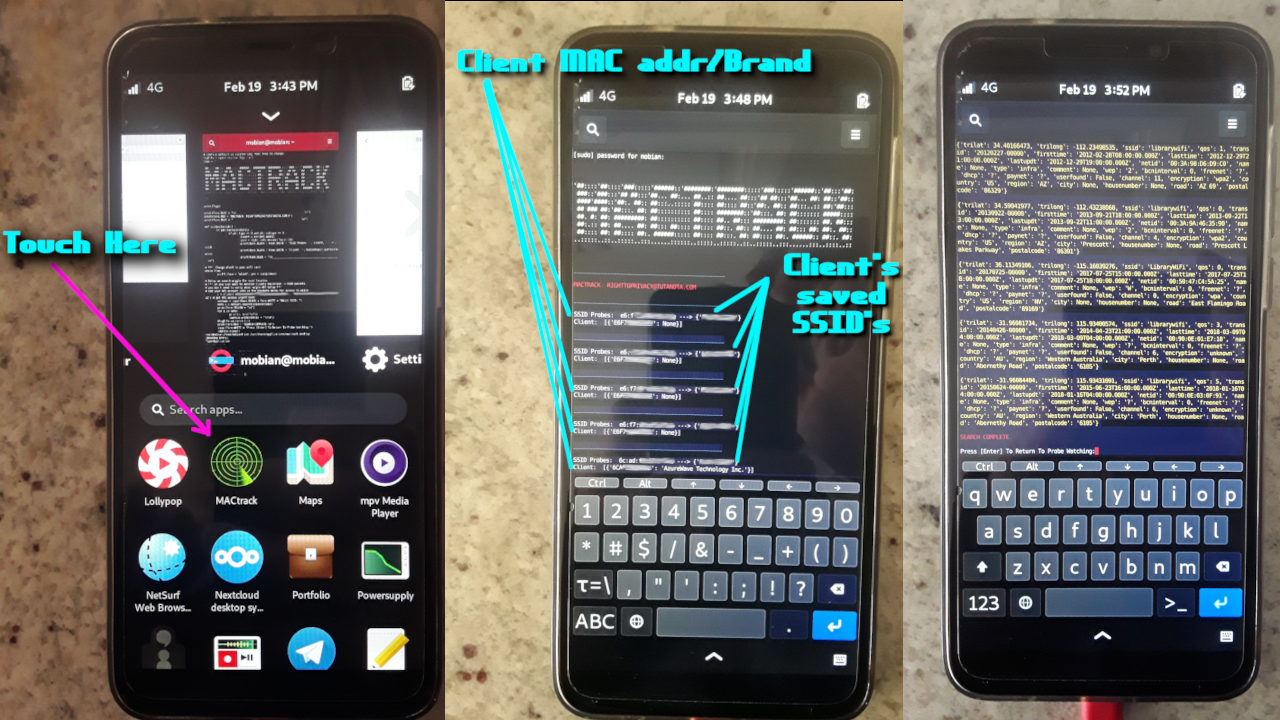
One could identify a masked burglar using this 'gadget' like button, showing not only their phone's mac address/brandname, but also their saved wifi networks, up to searching to find their street address/gps location.
I appreciate everyone following along and especially taking the time to Share, Like, and Subscribe. Every bit of help moves us up rankings/algorithm is motivating and appreciated. :)
I look forward to logging/sharing the progress with everyone.
MACtrack
DOWNLOAD HERE:
https://www.gitlab.com/Aresesi/mactrack
Or find it on my Odysee channel: https://odysee.com/$/invite/@RTP:9
[To install automatically: run the install.sh script in the mactrack directory after editing the wifi device variables and locations to match your OS];
MACtrack listens to (disconnected) nearby clients looking for their previous history of saved autoconnect networks. This means when a device comes close to you, you will see network names of the devices "Home", Work, the coffee shop, anywhere a device might have used wifi. All of those network SSID's are easily picked up over the open air, and the metadata can be relational to the OSINT search. MACtrack lets you search for the street addresses of those networks (tracking devices movements).
MACtrack prints all (disconnected from WiFi) client mac addresses and their history of saved WiFi network SSID's. This is automatically printed on the screen. MACtrack also prints out the brand name of the client. This can help you further identify the suspect/intruder (iPhone, Android, other devices).
When you see a client/SSID of interest, hit ctrl+c. This drops you to an SSID location search prompt (uses wigle SSID location/OSINT database). Entering an SSID of interest and pressing enter reveals all known GPS/street address locations of that SSID name. This is a small example how the protocols our device use give off metadata, which in turn can lead to mapping out our movements.
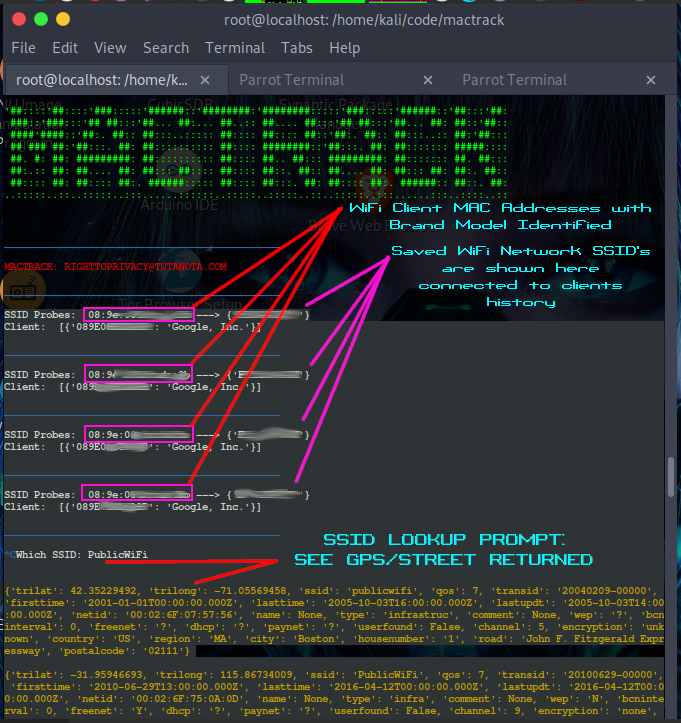
What does it do? MACtrack runs in a continual loop until you exit. So it starts out only printing (disconnected from wifi) clients->ssid's on the screen (with mac address + client brand). This means you will only have information on devices NOT connected to wifi. This means you will only have the clients of interest- not your neighbors or household members. Then when you hit ctrl+c you are dropped to MACtrack's ssid search prompt. It prints results to the screen and automatically saves them to a logfile for your later reference.
There are more features I will be adding to MACtrack, and I am thankful for this months supporters helping me out with minor sdcard/coffee :). I will be sharing new creative ways to use MACtrack here on BMAC.
Here is where to download the source to MACtrack:
HOW TO USE:
The install.sh script will put everything where it needs to be, creating the mactrack command and placing the Phosh icon on the desktop (for those using Linux phones/tablets).
You need follow the wigle instructions to get access to search database (for searching location). Although you still can use the probe listener without wigle setup.
For database search:
Setup a wigle.net account if you would like to use the location/gps/street address lookup feature. Add your API info to the line that begins with 'c ='.
After setting up your API info into the mactrack script line calling for it, you are ready to run it! Just tap the "radar" button on your desktop interface, and mactrack will put the WiFi card in monitor mode, and start printing out packets showing client mac address, it's brand name, and ctrl+c brings you to the OSINT GPS/Street address search prompt.
At this point it is ready to use!
OPTIONAL: If you do not follow install.sh script:
First make sure you to install the needed modules for full functionality:
pip3 install yawigle && pip3 install scapy && pip3 install OuiLookup
To get access to the SSID location search prompt database, make an account on wigle.net and then add your API information into the code (let me know if you need help here).
NOTE: to use both the listening part, and the lookup part at same time, it helps to have a 2nd internet enabled device. For example on a Linux phone like the Pinephone: cellular modem can be used for SSID lookups + wifi for listening. Will be sharing with everyone progress/use cases there.
Now change the variable inside mactrack to match your wifi card (as of this post it is wlan1mon- you can use grep to find the line).
Set MACtrack to be executable:
chmod +x mactrack
Now you are ready to run it (I will be adding parts of setup to the code for next version)!
Run it:
./mactrack
You can turn it into a command on your Linux machine by moving it to /usr/bin.
How to prevent MACtrack from identifying you:
While MACtrack can help identify anyone with a cell phone (with wifi not turned off), we may not want it used on us. I try to offer a solution with every example problem.
Prevent MACtrack From Tracking You:
⭐ UPDATED TIP: created solution for everyone -- the -w flag on wipri. This flag turns off wifi radio automatically when you leave saved network range after specified counters timing. Turning off WiFi radio automatically, anytime you leave home with -w set (can start at boot). This solution prevents any WiFi identifiers from being shared after a few minutes away from home (and won't disconnect you from current network).
You can mix the -w flag with other identifier disinfo flags included in wipri.
📁 Download Wipri (use Tor browser or torify git clone)
For Those Without WiPri:
Login to your wifi router as admin
change the SSID of your network to something more vague or common to throw off listeners
wipe the saved networks from your phone/pc and save only your newly created wifi network
for additional confusion for mactrack, save wifi networks found far away on wigle database; this leaves a trail of disinformation
Let me know if you need help and thank you again to all supporters/followers!
I have tested mactrack on the Pinephone (but to use both listening + lookup at same time calls for recommendation of 2 network devices: 1 for the internet wigle lookup- you can use cellular for this on the Pinephone, or a 2nd wifi device).
Until next time,
Cheers 8-)
😀 Thank you for Sharing this (Telegram/Social media + everywhere).
----------------------------------------------------------------------
🔐 ANONYMOUS GITEA (.onion): Books, Code/Scripts, Wiki, more (make a repository)
🔐 PASTEBIN (.onion): options- password protect, zk-256bit, "Burn After Reading" + more
----------------------------------------------------------------------
SUPPORT OPTIONS
(If you like)
🎁 EXTRAS: Unique extra Services (get something back for your support)
💲CASHAPP: $HumanRightsTech
✍🗒🎞 Politictech (monthly coffee option)
💳 Politictech Main Page: (info + current Crypto addr)
✍🗒 Politictech Blog: (Search Posts, read by category)
----------------------------------------------------------------------
FOLLOW:
✍🗒MASTODON
🐦 TWITTER
🎞 PEERTUBE
🎞 BITCHUTE
🎞 ODYSEE
---------------------------------------------------------------------
✉ CONTACT
-------------------------------------------------------------------------
THANK YOU for Sharing this, Liking, and Subscribing.
-------------------------------------------------------------------------
If you aren't registered for Odysee I'd love to see you over there.
Use my invite link: https://odysee.com/$invite/@RTP
--------------------------------------------------------------------------
