ADDITIONAL INFO: coreboot is safer than proprietary BIOS / UEFI on brand new computers.
Presenter uses coreboot for a specific reason: open source makes their example straight forward. Starting with open source firmware makes creating a proof-of-concept hardware backdoor much easier.
coreboot / libreboot (fork), from trusted source (or compiled yourself) makes hardware "more open", not less. Comes down to personal risk assessment - ask yourself: what might proprietary firmware be hiding?
For those sharing physical access to their motherboard, risk is equal (ie: malicious actor at repair shop). Something worth considering (if turning your computer over to complete strangers). Brand new computers can acquire supply chain backdoors - or may later become 'patched' (with malicious intent).
What can we expect in the future? Look to the past: learn from history. Post provides real-world examples, to share what could be on brand new proprietary firmware. Reasons to seek out open source hardware / software. No matter the platform / arch.
Came across this video today. Thought others may find interesting.
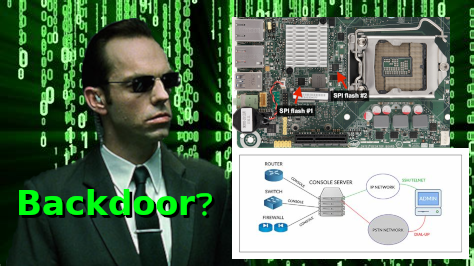
BACKDOORING BIOS FIRMWARE SLIDESHOW
BIOS / UEFI firmware is persistent.
HOW SO? Even if one overwrites (or removes entirely) all form of SSD / harddrive storage devices, problems (if maliciously compiled into firmware & flashed on motherboard) remain (aka "persist").
This is hardware persistence. Staying power.
BIOS / UEFI storing itself on motherboard. Not internal / external storage capacity.
At the same time, a trustworthy source can make hardware safer than brand new (such as coreboot - one reason it popular, making hardware "more open source", overwriting potential supply chain firmware backdoors).
A Nice Reminder: just because something is derived from open source software, doesn't automatically make it safe. Same holds true for all hardware / software (especially randomly downloaded precompiled roms - which I don't use, personally compiling where possible).
Randomly downloaded precompiled roms on random githubs and otherwise, could be hiding something, and provide an amazing opportunity to spread hardware backdoors through download alone.
One precompiled that is more well-known / trusted is Skulls. We're not talking about Skulls here, but the many random user precompiled roms presented for free download. Could some have backdoors?
Must always first completely "trust the source" (for any given piece of hardware / code). Maliciously modified laptops may present themselves as something: "too good to be true". Promises or prices that don't quite add up to the level of labor involved should be looked at with a discriminating eye (ask for evidence when presented extraordinary claims).
Superfish Example
As in Superfish / ASUS motherboard example, "brand new hardware" is not necessarily safe.
Superfish was a supply chain BIOS backdoor discovered in 2015 which broke https (even if reinstalling Windows... appearing secure with green padlock) for 40million (brand new) Lenovo Windows computers. With persistence. The only way to rid yourself of this backdoor was to overwrite BIOS flash chip/s (as in coreboot).
⭐ See coverage 4 years back on Superfish Supplychain BIOS backdoor: HERE
What's unique about this (case): Superfish BIOS backdoor overall allowed (the possibility) for plausible deniability: introducing a 2nd company (provides cover) for utilizing https stripping - a "parental control" front-end: this would (hypothetically) allow said backdoor to be explained away, as both "advertising based https stripping" & "parental control" https stripping under another company.
When "plausible deniability" is incorporated into malicious software, could be looking at nation-state activity.
⭐ Video on discovered / "official" shares hardware backdoors (by function, not proof of intent) providing (potential for) plausible deniability HERE
The Lesson: We have no idea what is yet discovered on brand new hardware with proprietary firmware. For x86, consider libreboot / coreboot.
⚠️ buy from hardware sources you feel you can trust. New or used. coreboot / libreboot, or not.
What is yet discovered in new hardware (with proprietary firmware) is most concerning.
Buying computers from random strangers (even coreboot as this video displays: ensure you trust) comes with risk.
Brand new hardware: risk remains (though might be higher if unlucky enough to buy from a malicious party] - can't help but wonder: how common might this be?).
Things similar to Superfish yet be discovered in brand new hardware.
Consider the ASUS motherboard UEFI backdoor from 2022 (mentioned in video).
Or even the multiple company routers containing matching backdoors in this video.
There are reputable coreboot laptop sources out there (as well as Arm and now coming RISC-V options). I share a list of (not sponsored - sharing personal opinion) suppliers I would personally consider using here (scroll down towards bottom for list of known trusted suppliers) [alternatively, you can find coreboot laptops offered right here, supporting public tutorials, very limited service].
One thing you may like to look for (for maximum safety), when seeking out safer x86 / Intel laptops: does the manufacturer document problems in hardware? Do they take extra steps towards closing off the aforementioned risks (such as Intel management engine removal / neutering)? These are good signs, but so is reputation.
If price is no issue, one manufacturer stands out: Talos II from Raptor Computing (PowerPC). These are pricey, but you get what you pay for.
You can alternatively choose another option from the list I created of coreboot laptop providers here.
May as well throw this in: limited number refurbished coreboot laptops currently offered here on public blog / channel, very limited availability service.
Simple official"disable" is in fact a temporarily disable - and not removing all possibilities.
Intel Management Engine running (even) when machine believed "powered off".
As we know with other security subversion trends: if something can be done, it will be done.
If nothing else: eventually, someone will try.
All we know is what has been documented thus far.
Proprietary closed source nature prevents us from knowing the true extent.
For all we know, there could be potential for reactivation of Intel management engine, at some level (hypothetically).
Of course, in the end, we only know what has been documented: some of this comes down to personal opinion / risk assessment.
BACKDOORS UNCOVERED IN BRAND NEW HARDWARE
Some of the backdoors (by function, not proof of intent) discovered over the years in brand new hardware are covered in this video (not found on youtube). One of the videos I recommend everyone watch, to get an idea of how these things can work, and what may be hiding:
What's nice about coreboot / libreboot, it overwrites bios firmware and provides open source replacement (where possible).
Use open source firmware where possible for your devices. These were a few design examples of what could potentially be hiding .
On a lighter note, follow Arm / RISC-V device progress.
You can watch my Pinephone content in the posts section. Click on "Linux Phone".
These are things to look forward to.
Ordered a Pinetab2 and should hopefully get it sometime soon. Though it's not known how usable it will be (yet).
Will share my thoughts on Pinetab2, here on the blog / channel. Looking forward to comparing it to the original! 😀