Coming Up Over The Next Few Videos We Will Look At Online Options, Linux Security / Radio
UPDATE: This post updated March 23, 2022 to include addition information on 'trilateration' location tracking. After sharing previews.
Hey friends, :)
Weeks ago I shared a couple people a sneak peaks of: wipri-list.
A new (optional) command inside WiPri (download latest on our 🧅🔐 Gitea Onion - use Tor Browser to access)
Managing many Linux devices had me annoyed at the fact even I did not recognize my own devices throughout my networks (using WiPri). Thankfully, Linux makes creating solutions easy! I still wanted the benefit of valid yet random mac addresses, but this time, those I could recognize.
One solution I had was to create quasi-permanent MAC address lists. To allow users to use -a flag to create and add (as many as they like) new MAC addresses to this list. -r to remove individual MAC addresses, -l to list, -s to set a randomly chosen mac from the list.
And I incorporated the mac leak prevention concept (created for wipri) into this in order to prevent mac address leaks. This is not to say you can't use another mac address changer on top if you wish (but wipri will ensure wipri mac's stay set).
If you wish to have a single permanent false mac address for a machine, simply run wipri-list -a to create the first mac address, and then you will have a single, permanent random, yet valid mac address.
And that is wipri-list. See the video for more general tips on wireless privacy.
For example I haven't had mac address leakage with it (as intended), but you can still set NetworkManager to 'random' if you like - it won't interfere.
The concept as well was mentioned as something of interest by a couple commenters. I always welcome good ideas, and if I think enough people may want to use something, I may go for it!
(comments, question or suggestions, welcome).
Looking forward to sharing new ideas, scripts, and images.
(To everyone who follows, and Shares. You're a big help. The algorithms don't always share unique content. Following is free, and allows you to optionally receive most unique posts by email)
Did you know Department Stores and many other locations around your area are constantly logging your current mac address, along with other identifiers like signal strength (used for trilateration: explained below)?
These mesh-like wireless tracking device networks work in close cooperation with your phone apps, communicating with "ultrasonic audio beacons", to send advertisements to your phone (sometimes from your TV!), based on what isles you idle, when inside a shopping store?
Yep. It's true.
And there is much more to this story...
Watch below at your choice of mirrors and don't forget to Share this article/video!
TODAY: WIRELESS PRIVACY TIPS + THOUGHTS
CLICK IMAGE FOR PEERTUBE (DECENTRALIZE/FEDERATED):
[ Odysee / LBRY ]
[ Bitchute ]
[ Youtube ]
Watch right here:
WiPri-List Screenshots:
Generate + Add new valid OUI mac address to the current quasi-permanent mac list (wipri-list -a)

List Our Current Created MAC List (wipri-list -l)
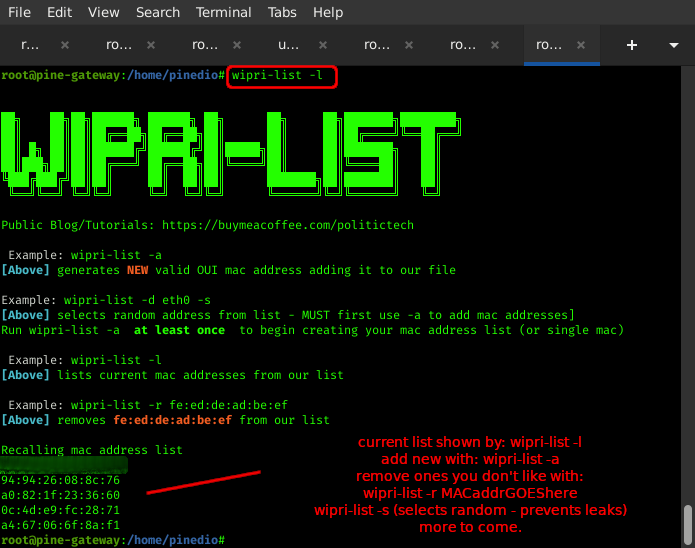
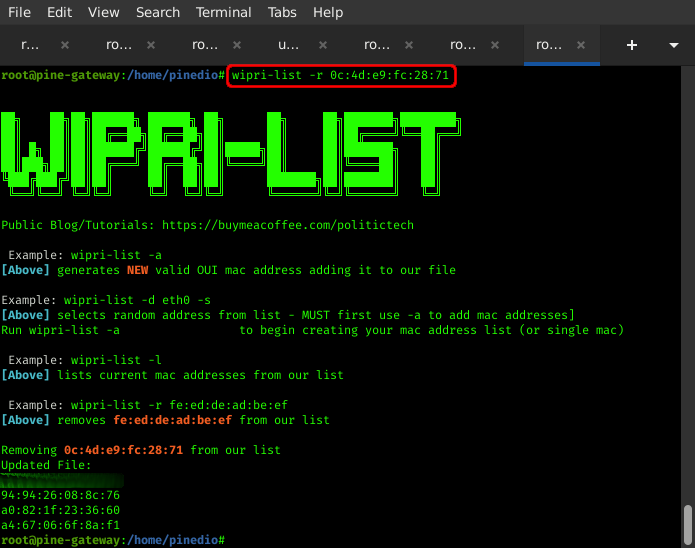
Remove Specific MAC Address From List (wipri-list -r 00:00:00:00:00:00)
Setting A Randomly Chosen MAC From List + Protect It
With this wipri-list -d [device] -s flag, you can have 1 or as many mac addresses in your list as you like. In this example, one is in the list: installed at boot, this creates a single quasi-permanent mac for this machine. If a user creates a longer list, each reboot (or service restart) selects a new random from the list.

For now, that's as simple as it gets. WiPri is still being updated (adding updates to Gitea onion the other day - older versions on Github/Gitlab; Always suggest the newest from Gitea Onion).
I'm taking into consideration other unmentioned methods of tracking, and putting some into play.
Signal Strength -> Direction ->
Location
In the video we cover briefly the subject of 'trilateration'. I wanted to discuss it shortly here to explain concepts behind -a and -s flags.
Trilateration is where a wireless (bluetooth, cellular, wifi) device's location is pinpointed by looking at the 3 receivers with the strongest RSSI signal strength.
Wireless Signal Strength Measurements

Various Nearby Devices (Within Range)

"Trilateration": 3 Wireless Devices Carrying Strongest Signal Location
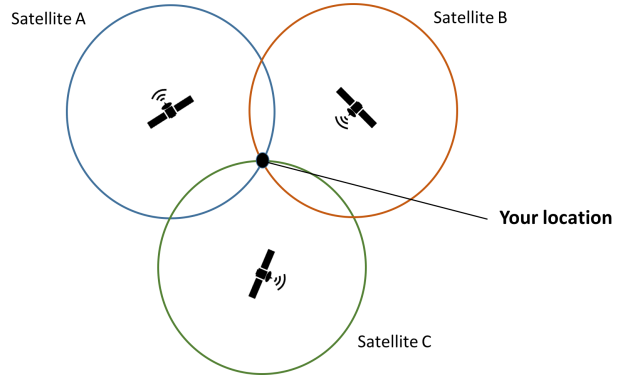
Trilateration
From here, location determination of a given WiFi/Bluetooth/Cell phone device determined by the "3 closest receivers".
The location of said device is normally likely in the middle of the 3 carrying the strongest signals to device in question (see above example diagram).
These sensors/receivers/towers collate signal strengths measure/share data in a cloud-like fashion, coordinating measurements with other identifiers (such as current mac address), to further isolate location. Similar to techniques used to catch those operating on Ham bands who aren't licensed.
Hence, original concepts in WiPri: options like -a flag, are offered to perform specialty functions: continuously changing valid OUI mac addresses, at continuously changing times/addresses.
In this way, trilateration + static mac address tracking can be mitigated (experimental). Along with other features not yet mentioned.
This is where the -s (signal continual randomization) idea came from (-a flag incorporates with: mac + hostname + signal: Experimental, but functional).
Continued...
Example of how -a flag on WiPri attempts to 'confuse' (experimental):
(-a ontinuously changing simultaneous hostname + mac + signal strengths)
This is not a feature most people need, but was one I wanted to play with, and could serve traveling (ex: connecting to various networks + sharing hostname is not privacy - many companies share data. If signal, hostname, mac change simultaneously, this can at least (in theory) make tracking harder). (Has been tested to vary signal RSSI)

wipri -d [deviceHere] -s is another option. This allows you to set a random signal strength changes. Flags make wipri commands handy to combine within other scripts.
That is a big reason wipri is flag based: to make it easy for you to add combinations at will to custom scripts.
Needless to say the signal strength continual randomization is considered experimental, a "fun" feature. And has been tested.
You can Download WiPri + WiPri-List and install using included install.sh script (boot start is optional, or select command use only).
Download WiPri / WiPri-List
DOWNLOAD OPTION #1.) Simply open THIS LINK in Tor browser To Download. That's it.
DOWNLOAD OPTION #2.) Commandline Installation:
Install the tor client:
Debian/Pop!_OS: sudo apt install tor -y
Arch/Manjaro: pacman -S tor
Next run:
torify git clone http://gg6zxtreajiijztyy5g6bt5o6l3qu32nrg7eulyemlhxwwl6enk6ghad.onion/RightToPrivacy/WiPri.git
That's it for today.
----------------------------------------------------------------------
💖 🤗 SUPPORT 💎 (If you like this you can now Monero directly below)
❤️ MONERO: (please see current: frontpage)
💳 🎁 EXTRAS: Support here for something in return - like your own privacybox: all in one encrypted pastebin + Nextcloud Tor Hidden Service Server/router.
🤑 💵 CASHAPP: $HumanRightsTech
❤️ 🪙 💎 Membership: private Nextcloud Tor Hidden Service "☕ coffee room" chatroom + file share, early/extra access, more
----------------------------------------------------------------------
📲 FOLLOW: ⏬
✍ 🗒 MASTODON
🐦 TWITTER
📺 🎞 PEERTUBE
📺 🎞 BITCHUTE
📺 🎞 ODYSEE
📺 🎞 YOUTUBE
----------------------------------------------------------------------
🖇️ LINKS / PUBLIC SERVICE 🔍
----------------------------------------------------------------------
🧅🔐 GITEA SERVICE (.onion): Books, Code/Scripts, Wiki, more (make a repository)
🧅🔐 PASTEBIN (.onion): options- password protect, zk-256bit, "Burn After Reading" + more (use Tor Browser for .onion's)
---------------------------------------------------------------------
✉ CONTACT
-------------------------------------------------------------------------
THANK YOU for Sharing.
-------------------------------------------------------------------------
If you aren't registered for Odysee I'd love to see you over there.
Use my invite link: https://odysee.com/$invite/@RTP
-----------------------------------------------------------
SUPPORTER THANK YOU
❤️ If you ever Support 6 ☕☕☕☕☕☕ coffees (whether 1 at a time, however, any period of time), or ❤️ monthly members 6+ months, and interested in supporter selfhost rpi image (.img) "extras", contact me.
Allowing more time, work, resources, code, servers.
Learn features (in Tor Browser) in: README.
At this time my plan is to keep making it better, finding new ways to dedicate more time! ❤️ I'm working on various things, almost everything (currently) public. Some not mentioned.
Here to teach solutions using Linux, FOSS, Privacy, and Human Rights topics.

