Thanks 'user', latest to join. Welcome. 🐧
🙌 First sent out to all my friends following on BMAC. Thanks for following / sharing.
✅ IMPORTANT: Be careful to set the correct block device (disk location) for the hardware key / encrypted $HOME volume. I recommend only trying this if you know what you are doing. And if you don't, don't be afraid to ask a question.
cryptohomes won't make any changes until you ask it to, using "make_vol" and multiple confirmations.
💡 If you have any questions, don't be shy: leave comment. I don't want to see anyone to select the wrong disk, harm files. Check device size to select correct devices. Your question could help others in the future.
Started (1yr ago) as idea to play with on Pinephone (works on any Linux device/computer).
Sounded like a fun project. Got back into it lately (as time allows).
Past Video Demo
Hope you find useful (though more improvements to finish). 💻 🐧 📲
📁 DOWNLOAD (🔐 On Gitea Onion: Use Tor browser)
🔐 CRYPTO_HOMES
Automatically Create Hardware Key (usbstick) + Encrypted Compartmentalized $HOME volumes
crypto_homes offers combined benefit options of automated compartmentalization, isolation, encryption (using any cipher available to your system).
Only hardware needs: Linux laptop or Phone / computer (2 disks of any kind: one to become encrypted $HOME volume [any disk], the other to become hardware key [any disk]).
🏠 WHAT IS A "$HOME"?
Since using $HOME interchangeably, let's define: "what exactly is $HOME?"
The $HOME directory is your local working space.
EXAMPLE: If you login as username "gary", $HOME is /home/gary.
To see your current $HOME, run:
echo $HOME
Your $HOME is where you generally save files, downloads, pictures, etc.
It's the "computer storage" for any given login username.
By making a separate encrypted $HOME encrypted volume disk, we create a bit of a portable stored "setup". We can change the look of our desktop, among other settings. Staying inside the disk.
REQUIREMENTS
single Linux phone or laptop, computer, singleboard computer (Linux device of your choice)
the disk you would like to become a hardware key (any disk will work, sdcard, usbstick)
the disk you would like to become your new encrypted $HOME volume
By default, you are asked to create backup password, in case you lose your hardware key (can delete password later if desired).
🖼️ SCREENSHOTS / 📝 TUTORIAL
To start, download crypto_homes from the Gitea Onion.
INSTALLER
(optional, but suggested, for persistent access to crypto_homes command)
Usage of included install.sh script: optional. Creates system-wide crypto_homes command for your system (this way crypto_homes command is retained, for your new $HOME)
Remember: it's a fresh space, no crypto_homes or files from your old $HOME will be present once booting in (unless you use the installer, creating a system-wide crypto_homes command).
Don't worry: you won't lose your old $HOME directory / files, they simply won't be present in the same boot instance.
Revert back to booting original $HOME directory, anytime you like.
🔐 INSTALLING CRYPTO_HOMES AS NEW COMMAND:
sudo bash install.sh
screenshot:
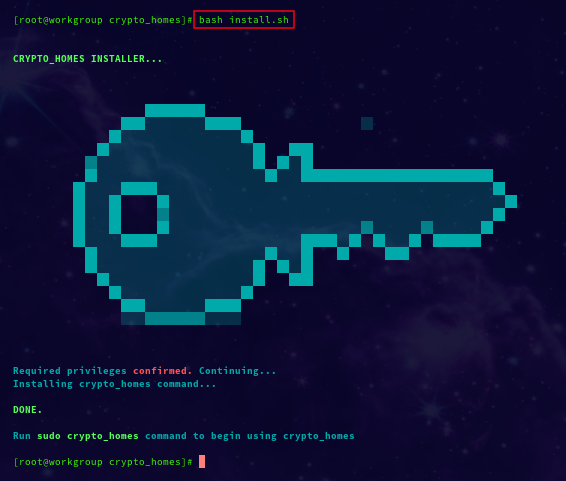
Why The Installer?
Sure, you can run bash script cryptohomes.sh locally. But once you create the encrypted $HOME disk, you become transported into a fresh new $HOME environment (without the crypto_homes download from previous $HOME in that space).
Nothing you download or change occurs to original home directory. Downloads will be stored on the encrypted $HOME volume disk anytime you are booted into it.
The old $HOME (ie: /home/user) still exists on your main SSD / Harddrive disk (with all previous work, as you left it, untouched). As long as you don't select the wrong disk.
New encrypted $HOME volume comes with what's needed for $HOME. Ready to accept changes to (new) local user config / files, $HOME directory (ie: /home/user), environment.
BENEFITS
One, you have additional space you wouldn't have otherwise, and a safer $HOME, given if your main disk fails, you lose nothing on the encrypted $HOME disk.
Essentially, making a new $HOME disk + hardware key creates a new virtual workspace for whatever your needs are.
What if you lose your phone?
If a Journalist, you may need to protect work / sources when traveling.
You can gamble with the safety of your small business, corporate, or personal data, or you can improvise, creating new virtual workspaces / encrypted volumes.
This way you can (optionally) leave this user setup / work at home, or take the disk, only opened with password (can delete) or hardware key.
🖥️ 💾 FRESH USER COMPUTER SLATE
When running off newly encrypted $HOME volume, you start with a fresh slate. Configure a new looking desktop if you like. Retained on the encrypted $HOME volume.
Only loaded when in the computer with key.
Anytime, you can revert back to the original. Leaving all work, files, configuration, look of your desktop, safely stored on the encrypted disk.
💾 🔑 HARDWARE KEY AUTOMATICALLY UNLOCKS CRYPTO_$HOME
Anytime it makes a new virtual $HOME encrypted volume disk, it also creates a partner hardware key.
Choose any old usbstick (thumbdrive) or sdcard, for your new hardware key.
Your hardware key automatically unlocks it (at boot -- both encrypted vol and hardware key should be plugged in at same time, before booting in).
📝 GETTING STARTED
Once you have run the installer, you have crypto_homes as system-wide command (accessible from any user login, whether original $HOME, or encrypted $HOME volume disk).
Simply Run:
sudo crypto_homes
(example run below)
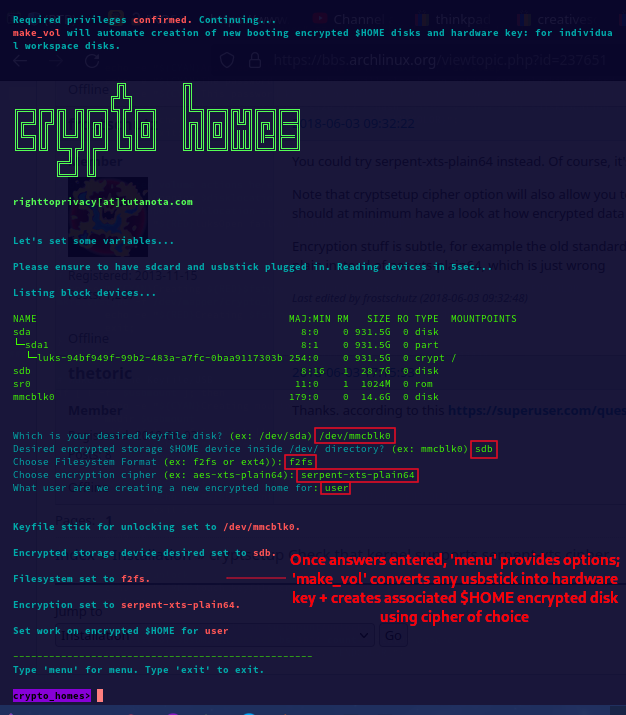
Above shows an example run inside the crypto_homes command.
At this time, it asks for a few details, to ensure changes are only made to the disks you intend.
There may be some revisions in the future, but currently this is how it begins.
🔐 CHOOSING CIPHER
Linux distros come with a selection of ciphers from which to choose.
We can use default aes-xts-plain64 (choose if unsure), to something more exotic like twofish / serpent (make sure to have available -- below for details).
Screenshot above demonstrates serpent-xts-plain64 (more on this later).
Check ciphers available by benchmark:
cryptsetup benchmark
screenshot:
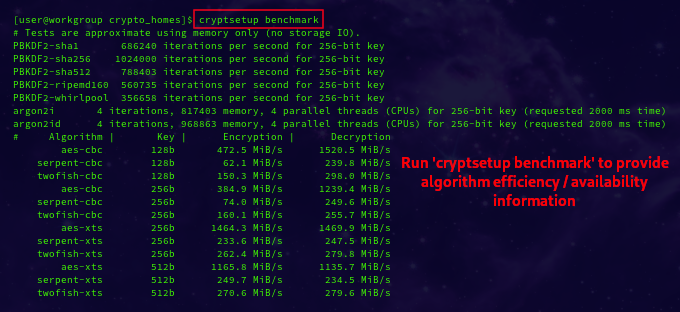
(see /proc/crypto)
💽 DISKS
Once entering disk desired as a hardware key (ex: any usbstick or sdcard), the disk you would like to become the encryped $HOME volume itself (any usbstick / sdcard), filesystem type (ex: f2fs or ext4), the cipher (ex: aes-xts-plain64), and login name (your linux login), we are ready to begin making our volume.
📄 MENU
Currently, a few options:
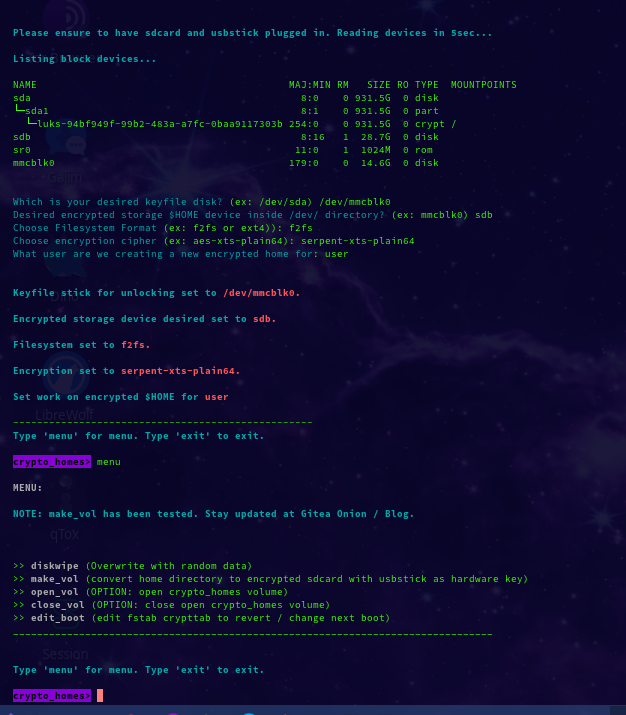
make_vol creates hardware key + encrypted $HOME volume automatically
open_vol uses plugged in hardware key to unlock encrypted $HOME, mounting it at /mnt/home as an unlocked encrypted volume (allowing work within /mnt/home as with any other file directory)
close_vol unmounts and locks the encrypted disk
edit_boot opens /etc/fstab and /etc/crypttab in nano text editor (change variable for vim if you like); this lets you add hash anytime in front of your new volume (adding hash prevents line from loading at boot)
REVERTING TO OLD $HOME BOOT
Crypto_homes is something I work on when I have time (between other work), tested, ready to try (covered some months back). If you aren't sure about something, leave a comment.
Make sure to comment if unsure (hate to see anyone select the wrong disk).
For reverting boot (to original $HOME), simply add hash marks (#) to your new volume inside /etc/fstab / /etc/crypttab to prevent system from loading the newly created hardware key / encrypted $HOME disks.
TIP: alternately, you can simply replace the new /etc/fstab with crypto_homes backup of original fstab found at: /etc/fstab.bak; original crypttab backed up to: /etc/crypttab.bak
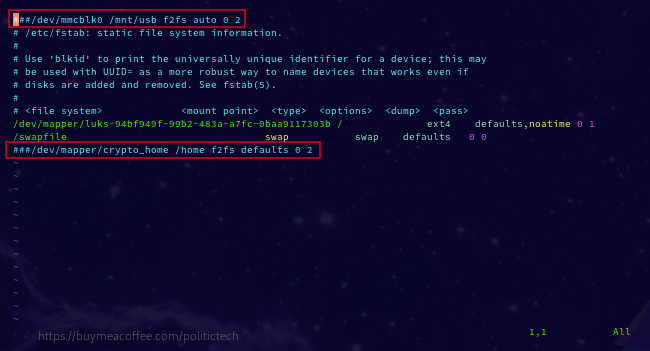
EXAMPLE HAND EDIT: To Boot Back To Original $HOME, hash out the lines for both the hardware key /dev/mmcblk0 (in my case), and the crypto_home line. By hashing lines out, your system will no longer load them, booting into the original, previous $HOME (the $HOME prior to creating your crypto_home).
fstab hashed out (note 2 lines are hashed out, for keyfile and $HOME encrypted vol):
screenshot example crypttab hashed out:
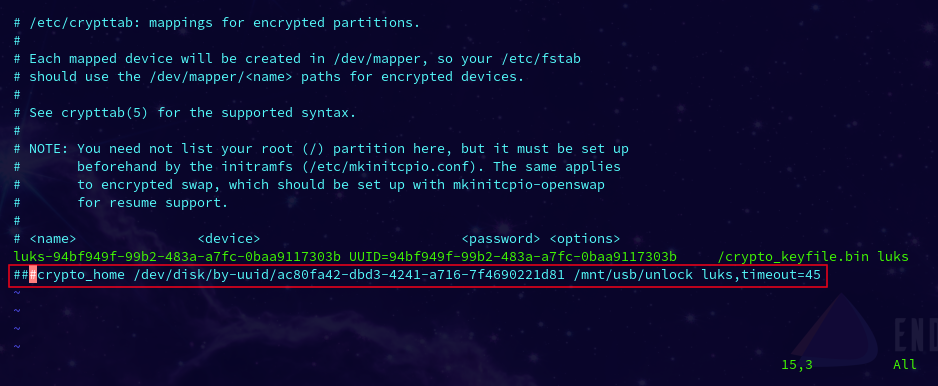
Anytime you hash out those lines (add 1 or more # marks in front), your next reboot will revert back into your old setup (by blocking the crypto_homes lines from loading at boot).
If you follow the above, next time you are ready to load your crypto_home:
plug in hardware key (usbstick or sdcard chosen in make_vol)
plug in encrypted $HOME disk (usbstick or sdcard chosen in make_vol)
delete any hash marks you added to fstab/crypttab (to have Linux load your encrypted volume disk/hardware key)
And reboot.
⭐ Make sure to SHARE this 🔗 Help unique content grow against algorithms not promoting this
📩 Email | 🧅 📨 Onionmail + 🔑 PGP (🧅 Tor Browser Link)
