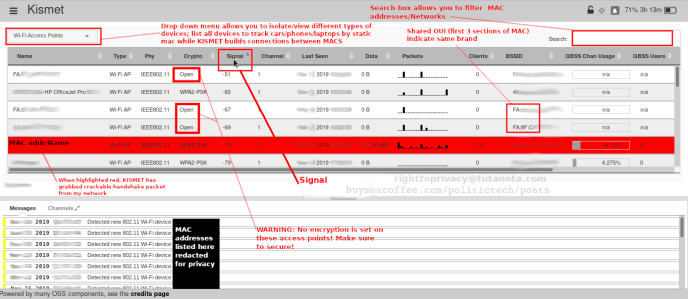
KISMET is an amazing tool for learning more than you think about closeby wireless devices and networks, even planes in flight (SDR, WiFi, Bluetooth).
Additionally KISMET will alert you to wireless attacks against your own network!
Functional as both a network admin sniffer, and simultaneous security tool. Detect hidden WiFi networks/devices to help root out backdoors from your network.
How to: Run KISMET sniffer off your laptop/SBC in a shoulder bag while remotely controlling & administrating everything: from your handheld smartphone web browser, for convenient (& mobile) analysis.
Presenting a small example of how wireless mac address/wireless device metadata tracking works using real-world signals intelligence (for everyone).
Your mac address and its saved identifiers are tracked in this way whether or not you ever connect to a wifi network -- including by your own home <insert big tech company> devices. Even delivery/map trucks map out networks and device mac addresses locations. This data is shared with 3rd parties, allowing real-time location tracking of device owner. Be sure to utilize tools to mitigate static identifiers (ex: wipri).
Before reading further, be sure you already have a working Monitor mode WiFi/KISMET setup. My recent video will shows the easiest path to working Monitor/KISMET:
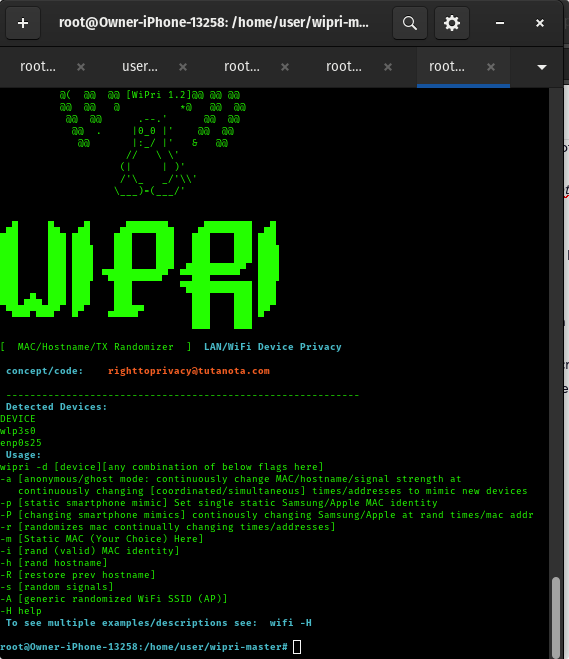
WiPri: Tool To Mitigate (common) WiFi scanning mac address tracking to protect your own devices:
WiPri (.onion download): Various flags from signal strength randomization to hostname, to mac address static/random (with check enforcing) continuous changing randomizations at continuous changing, randomized times/addresses (coordinated simultaneous to simulate new devices, or individual flags)
Administrating KISMET Via Smartphone
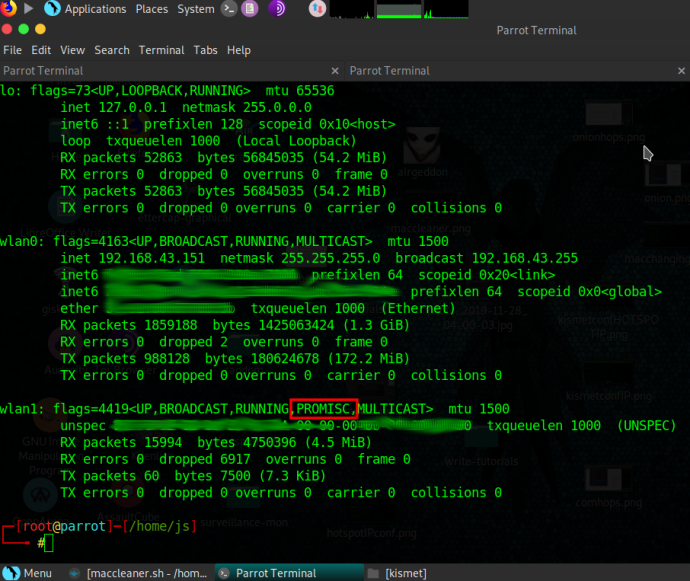
Put that card in monitor mode (for either laptop or single board computer running the kismet process) by running the following commands (in order):
sudo ifconfig wlan0 down
sudo iw wlan0 set monitor none
sudo ifconfig wlan0 up
DISCLAIMER: Only use KISMET to test your own network device behaviors & those you have permission to work with. This is a passive, but powerful tool. With power comes responsibility.
Administrating KISMET from our cell phone offers you freedom of movement during analysis. Instead of having to carry around an open laptop, we need only to carry our cell phone (and who isn’t always on their cell phone?).
To make the connection we will turn our phone into a hotspot, creating an LAN network between phone/laptop from which we connect back. Finally, logging into KISMET via our phone’s web browser.
PRESETUP
Requirements:
2nd wifi card on either your KISMET server OR the device you choose to manage KISMET with. (key here is you are creating an LAN with the NEW wifi accesspoint: either the KISMET browser machine, or the KISMET server needs to become a new wifi accesspoint.
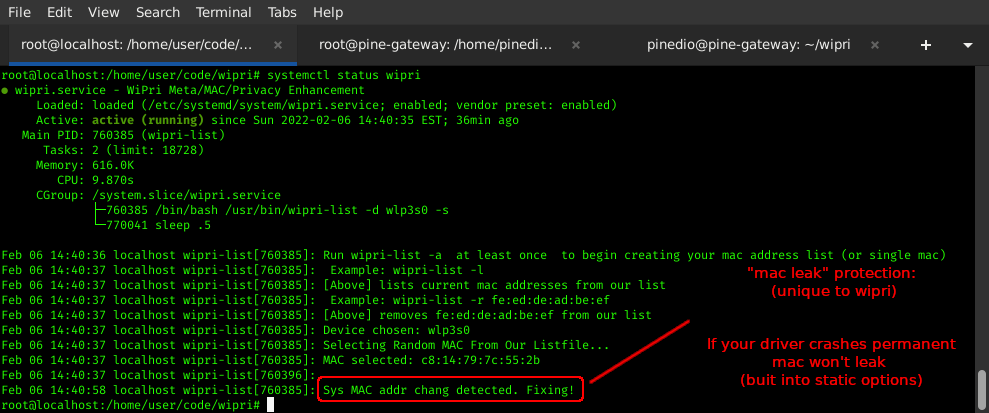
WiPri: used to prevent any permanent mac address leaks (use the static flag [-p, -m, -i] choices to prevent mac address leaking - static flags specifically are designed to prevent mac address leaks)
Use WiPri on BOTH client and WiFI Accesspoint mac addresses
SCREENSHOTS:
Commandline Usage Is Fine For KISMET Usage Or Otherwise:
Below Shows WiPri Preventing MAC Address Leaks On A Boot Install (SystemD):
Step 1.) Turn Your Phone Into A Hotspot. Connect laptop to phone hotspot.
Step 2.) Edit /etc/kismet/kismet.conf (or ~/.kismet/kismet.conf) to show correct phone’s LAN assigned IP/port (so kismet laptop knows who to accept connections from) & source KISMET listening wifi device on laptop to login via http browser as shown below:
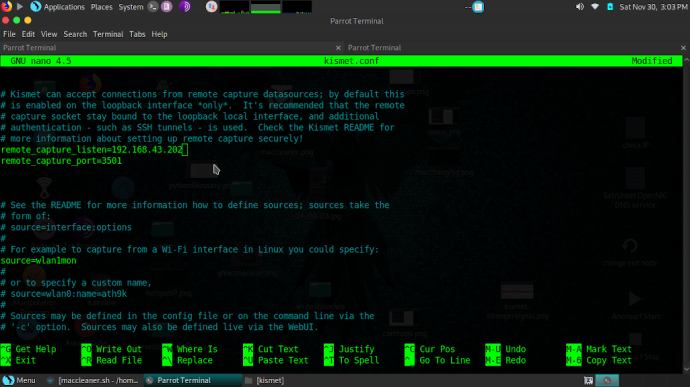
Step 3.) Edit:
/etc/kismet/kismet_httpd.conf
or
~/.kismet/kismet_httpd.conf
Inside the httpd.conf file, create your chosen username/password for your remote http browser login (from phone) as shown below for example (more secure encrypted logins covered in next tutorial of this series):
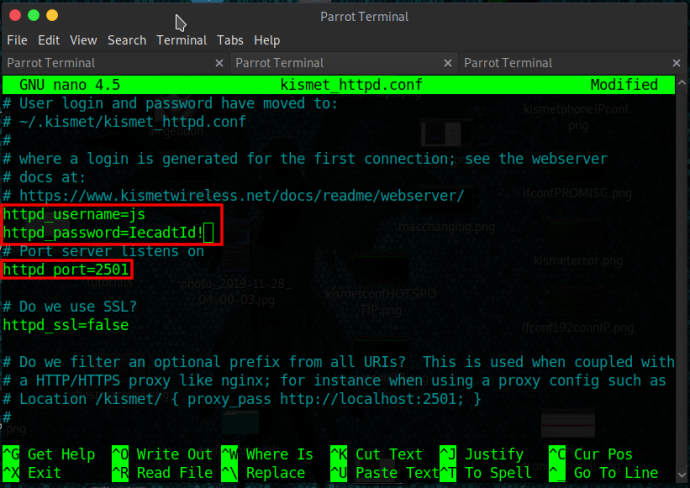
Step 4.) Start KISMET as daemon to run in background by issuing:
kismet --daemonize
Step 5.) Open your favorite browser on your phone. Type in the LAN laptop IP address with :2501 port connection extension (or another port if you chose such) as shown below in browser screenshot. Login using the username/password you setup in Step 3 in the kismet_httpd.conf file.
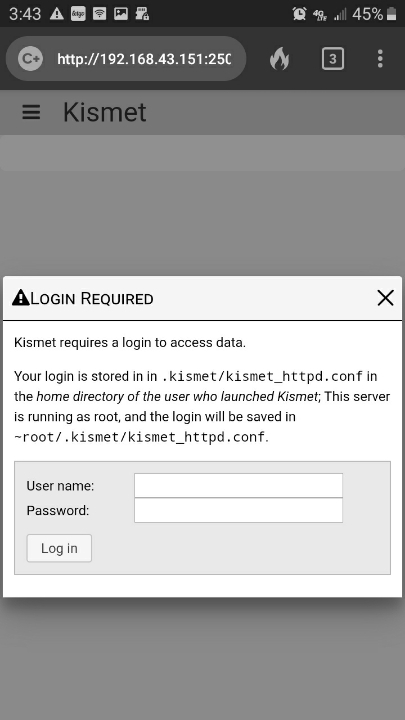
[ Now administrating KISMET from our phone - any phone will do! ]
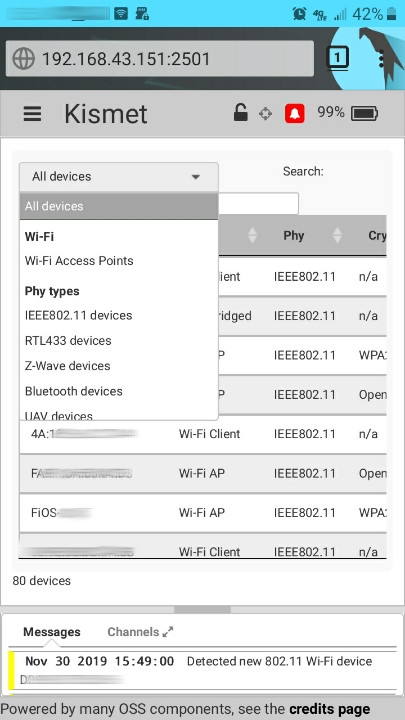
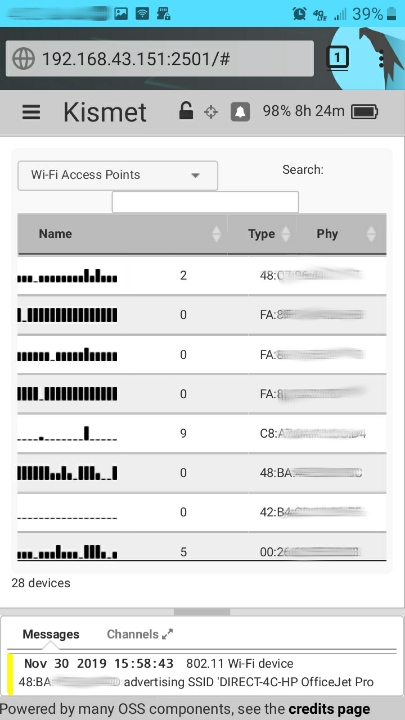
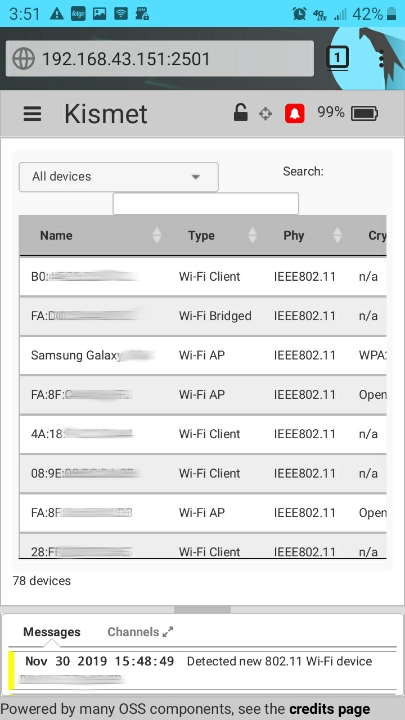
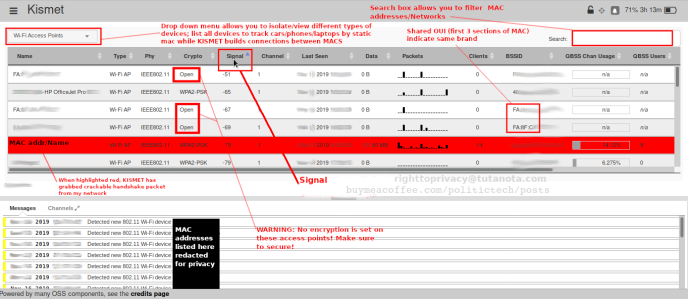
KISMET administration screen, labelled for your reference:
Step 6.) This next tip can be handy if you wish to walk around with KISMET laptop running in a laptop bag for example, while say, administrating KISMET from your handheld phone:
TIP: Right click your laptop power management settings - battery icon (likely in corner of your desktop). Select preferences. Fit your settings to match below so KISMET continues running while your laptop is closed in your bag, so you can administrate uninterrupted:
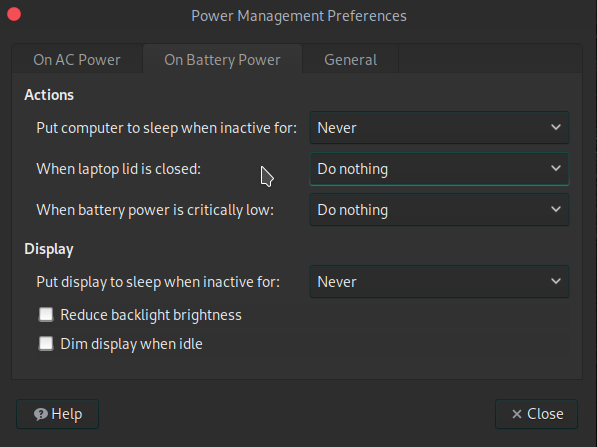
Now you should be all set to close up your laptop, put it in your shoulder bag & do all administration work from your handheld smartphone!
Coming up I have another unique tutorial for KISMET administration. Still collecting screenshots and look forward to presenting it.
Thanks for Sharing this. And to those interested in other Support options, they are right below.
Look forward to talking with you all. :)
-RTP
Thanks for reading and following/watching.
Thoughts, comments and any questions welcome below.
😀 Thank you for Sharing this (Telegram/Social media + everywhere).
----------------------------------------------------------------------
🧅🔐 ANONYMOUS GITEA (.onion): Books, Code/Scripts, Wiki, more (make a repository)
🧅🔐 PASTEBIN (.onion): options- password protect, zk-256bit, "Burn After Reading" + more
----------------------------------------------------------------------
🤗 SUPPORT OPTIONS (If you like to)
💲CASHAPP: $HumanRightsTech
✍🗒🎞 Politictech (BMAC Memberships (monthly supporter option)
🎁 EXTRAS: Unique extra Services (get something back for your support)
💳 Politictech Main Page: (info + current Crypto)
----------------------------------------------------------------------
FOLLOW:
✍🗒MASTODON
🐦 TWITTER
🎞 PEERTUBE
🎞 BITCHUTE
🎞 ODYSEE
---------------------------------------------------------------------
✉ CONTACT
-------------------------------------------------------------------------
THANK YOU for Sharing this, Liking, and Subscribing.
-------------------------------------------------------------------------
If you aren't registered for Odysee I'd love to see you over there.
Use my invite link: https://odysee.com/$invite/@RTP
--------------------------------------------------------------------------
